Information Security Risk Assessment
Risk Assessment
Software
Manage your information security risk with Tandem
Ensuring the confidentiality, integrity, and availability of information is vital to the operations of your organization. An effective IT risk management process should identify, measure, control, and monitor risk.
Tandem streamlines this process, so you can focus on reducing your organization's vulnerabilities and threat exposure.
Information Security Risk Assessment
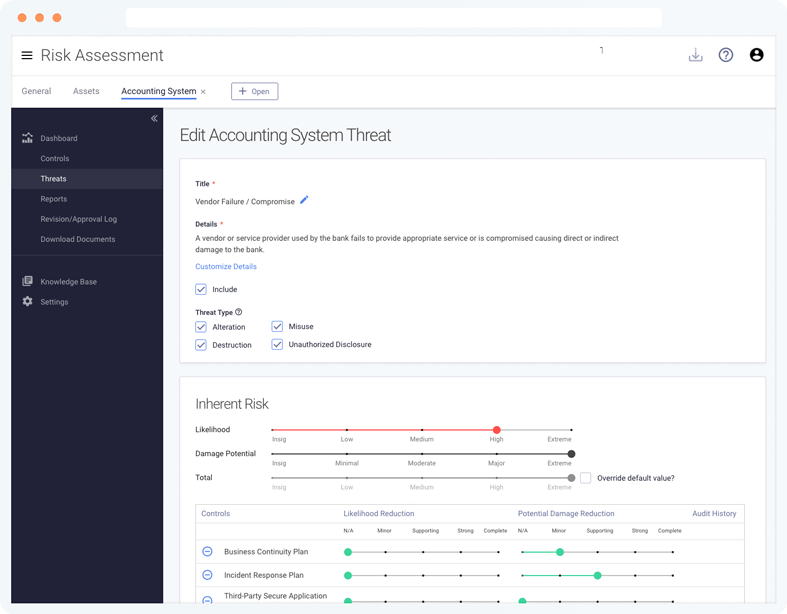
Start with our risk assessment template, which includes more than 60 common enterprise-wide information security threats.
Answer a questionnaire to unlock risk level suggestions. Then customize the risk assessment so it perfectly reflects your organization.
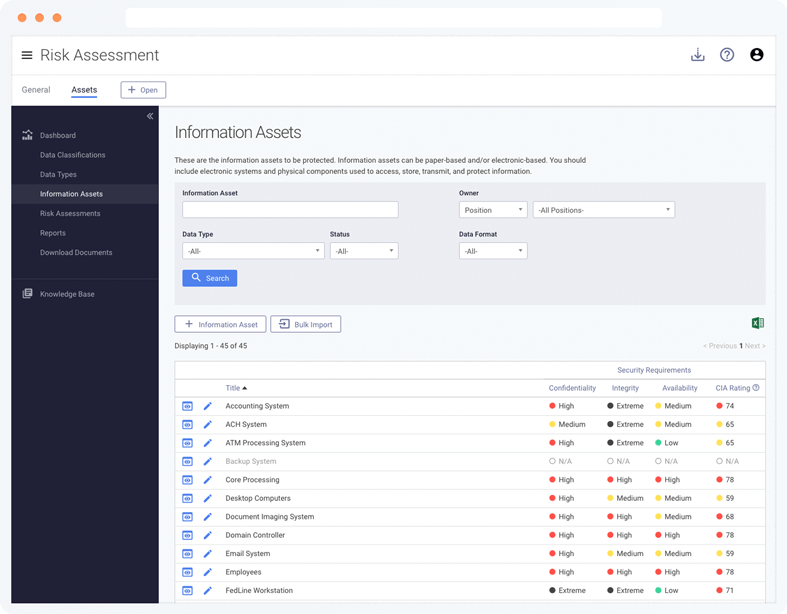
Information Assets Inventory
Maintain an inventory of your information assets and rate their confidentiality, integrity, and availability requirements.
Use the inventory ratings to determine the right level of protection for each asset.
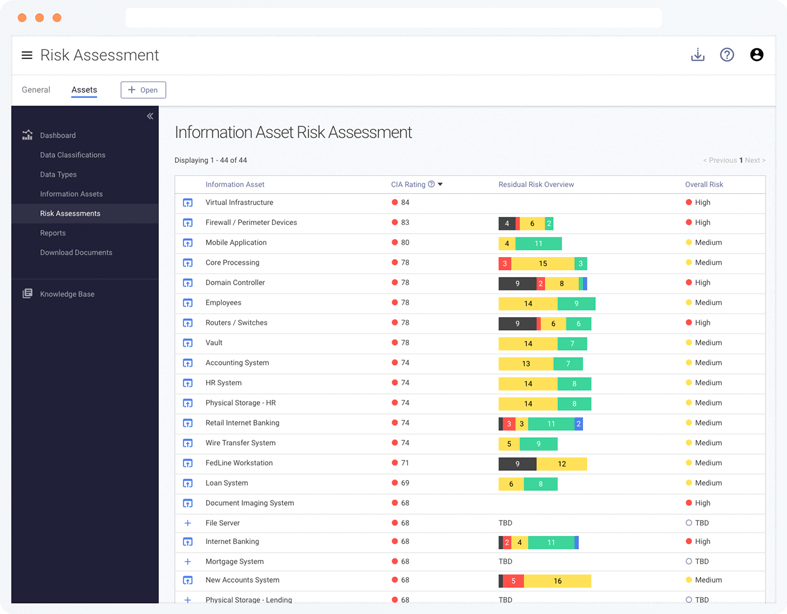
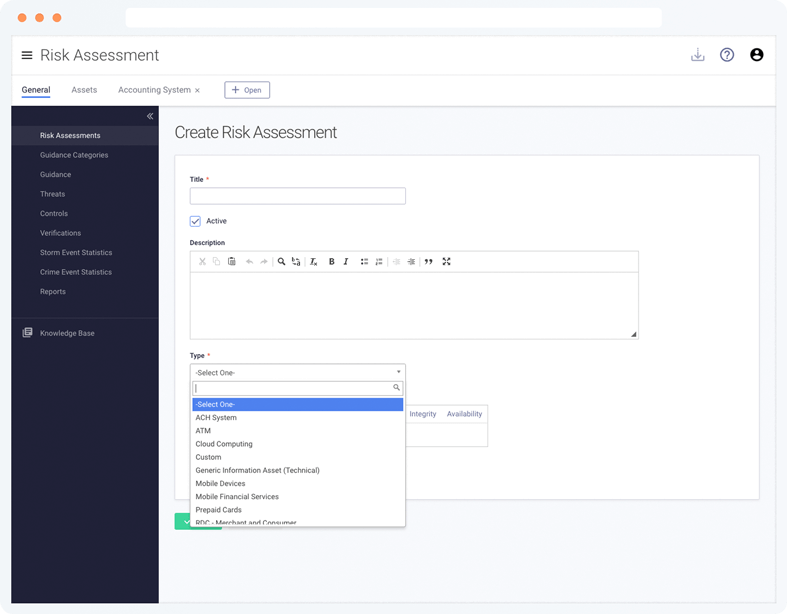
Asset-Based Risk Assessments
Once your priority information assets are identified through your inventory, efficiently conduct unique risk assessments for them using the Tandem framework.
Additional Features
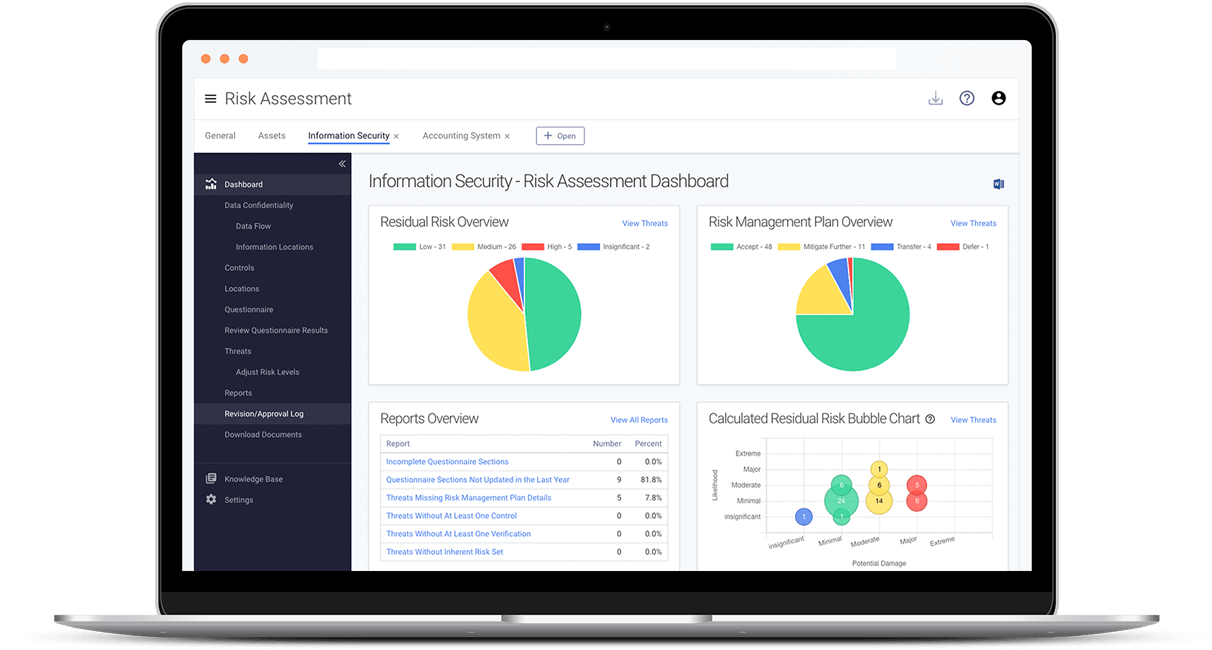
- Visualize your risk exposure with charts and graphs
- Document a risk management plan
- Access storm and crime event statistics for geographical threats
- Create an unlimited number of information asset risk assessments
- Identify gaps with reports
- Utilize suggested threats, controls, guidance, and risk levels
- View risk at a high-level across all assets or by individual assets
- Assign responsibility and various levels of access to users
- Receive a calculated overall risk for each asset
Frequently Asked Questions
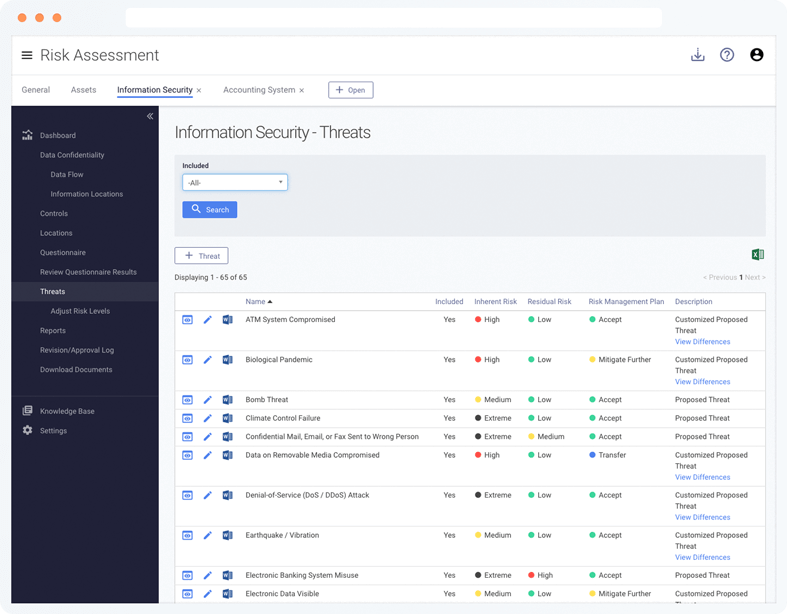
Yes. Tandem provides an overall information security risk assessment template with a list of more than 60 common enterprise-wide information security threats.
The results of this comprehensive assessment are quickly generated based on a questionnaire. Each threat includes suggested controls, risk levels and regulatory guidance.
The following asset-based risk assessment templates are also included:
Yes. Tandem offers a Knowledge Base with articles written by Tandem experts.
While you navigate the product you will also find help tips along the way.
Yes. Tandem Support is available 8-5 (CT) M-F to answer your questions about Tandem application features.
For help with the contents of your risk assessments, check out our partners who can provide risk assessment consulting.
You are also invited to attend our annual KEYS conference to connect with other users and learn from Tandem experts.
Tandem is pleased to offer complimentary training webinars each month for our customers. These webinars are recorded and available on-demand.
A Knowledge Base is available with articles to help you learn about Tandem. You can stay up-to-date on our latest features by subscribing to our Software Update emails.
Product training is also available by request for an additional fee.
Yes. Tandem maintains high marks through the following testing: SSAE 18 SOC 1 Type 2, internal audits and assessments, quarterly penetration tests.
Security controls include:
- Secure data transmission between your browser and your servers
- Data encrypted at rest using AES-256
- User passwords are hashed and salted
- Datacenter protected by firewall and intrusion detection/prevention systems (IDS/IPS)
- Redundant internet connections
- Multifactor authentication options
- Single Sign On (SSO) integration using SAML 2.0
- IP address restrictions
- User activity log
- User access roles/restrictions
Tandem products are delivered via the internet as Software-as-a-Service (SaaS) applications. Tandem can be accessed from any device with a modern web browser. No software installation or special equipment is required.
New features and updates are included with your annual subscription and are automatically available. Each new feature is documented in our Software Updates blog.
Yes. Tandem Risk Assessment integrates with other Tandem products to provide seamless sharing of data and help avoid duplication of information. All Tandem products are available under the same secure website.
The Tandem Internet Banking Security Program can be purchased separately and the risk assessments it includes are managed alongside your other risk assessments.
Policies contained in Tandem Policies can be referenced as controls in your overall information security risk assessment. This includes the customizable set of more than 40 pre-defined Information Security Policies, which are already mapped to threats.
Additionally, the asset management tool integrates with Tandem Vendor Management and Tandem Business Continuity Planning modules to show connections among assets, vendor services, systems and software.
Yes. With a single login you can manage several companies' risk assessments (requires a subscription for each company).