Information Security Policies
Policy Management
Software
Create and maintain your enterprise-wide policies with Tandem
Policies and procedures are the primary methods organizations use to define controls. Too often, policies and procedures end up sitting on a desk and collecting dust.
With Tandem Policy Management software, you can maintain a living set of policies that is easily accessible.
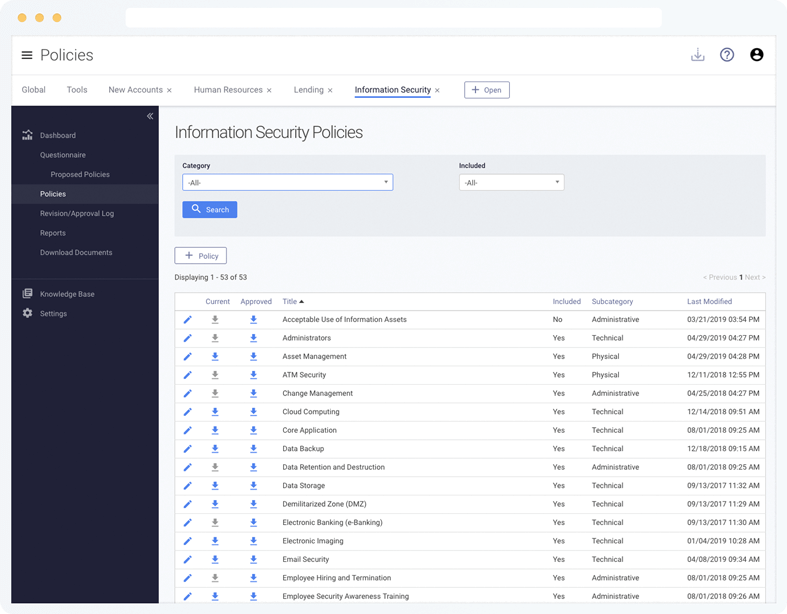
Information Security Policies
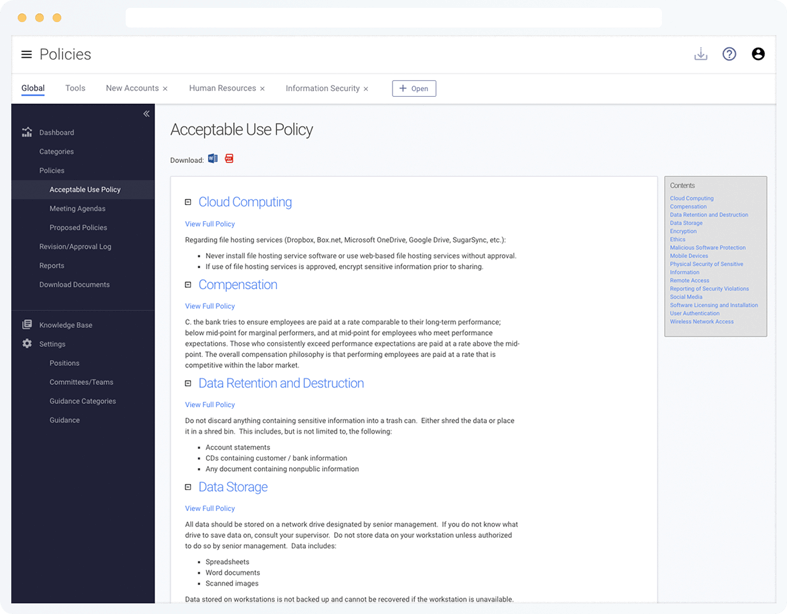
Use Tandem Policies to access a complete list of 40+ information security policy templates, created by security experts and tailored for your institution through a multiple-choice questionnaire.
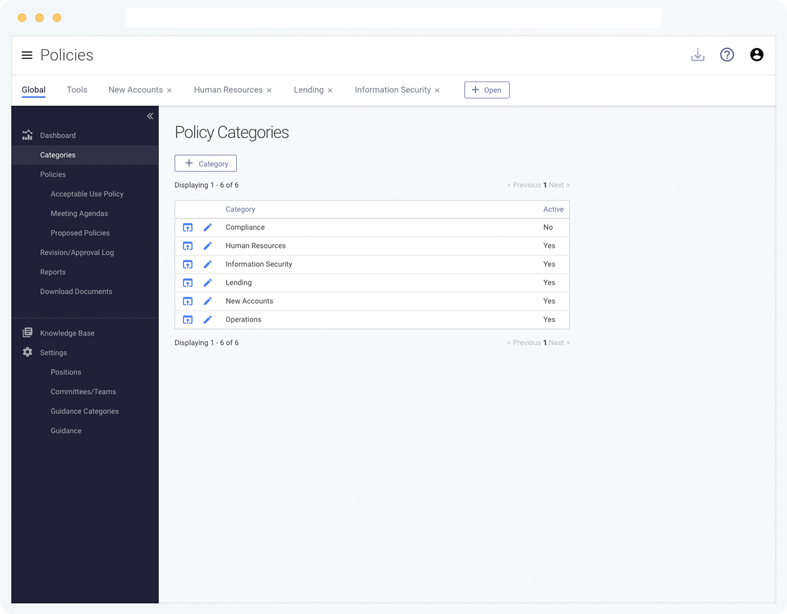
Enterprise-Wide Policies
In addition to Information Security policies, create your own custom categories (e.g. Lending, Operations, Human Resources, etc.).
While policy language is not provided for custom categories, you can add your existing language and use Tandem's tracking features.
Tracking & Oversight
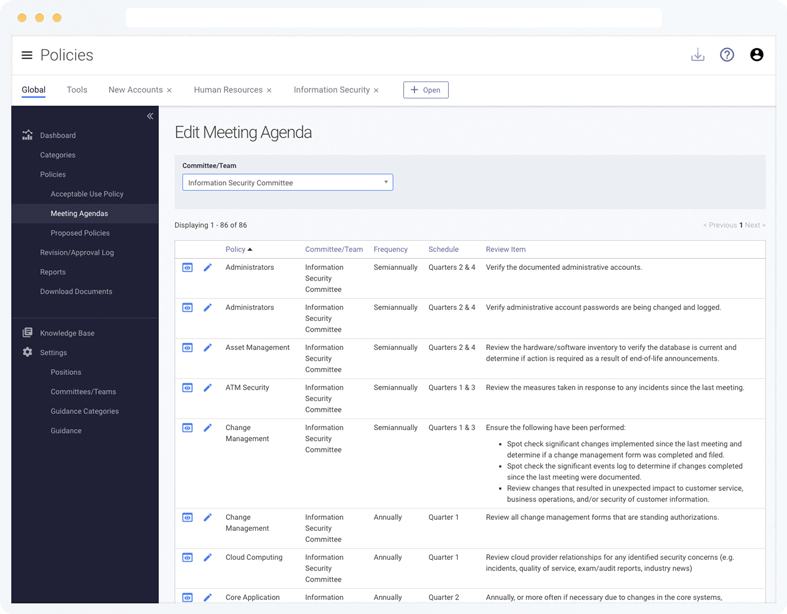
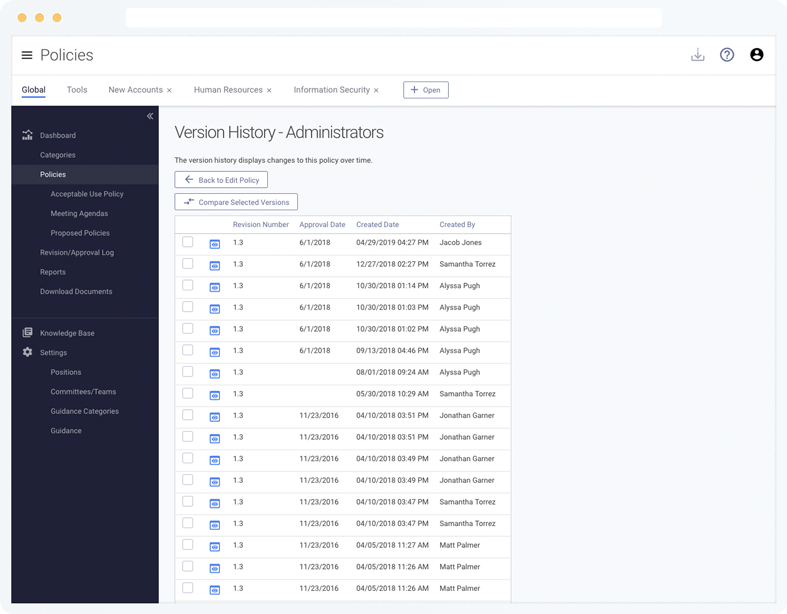
Never lose track of a single change. Every time a policy is saved, a version is stored in Tandem for comparing over time and reporting to the board.
Use the revision logs and meeting agendas to make maintenance easy.
Additional Features
- Maintain a complete revision history of policies
- Create a revision/approval log
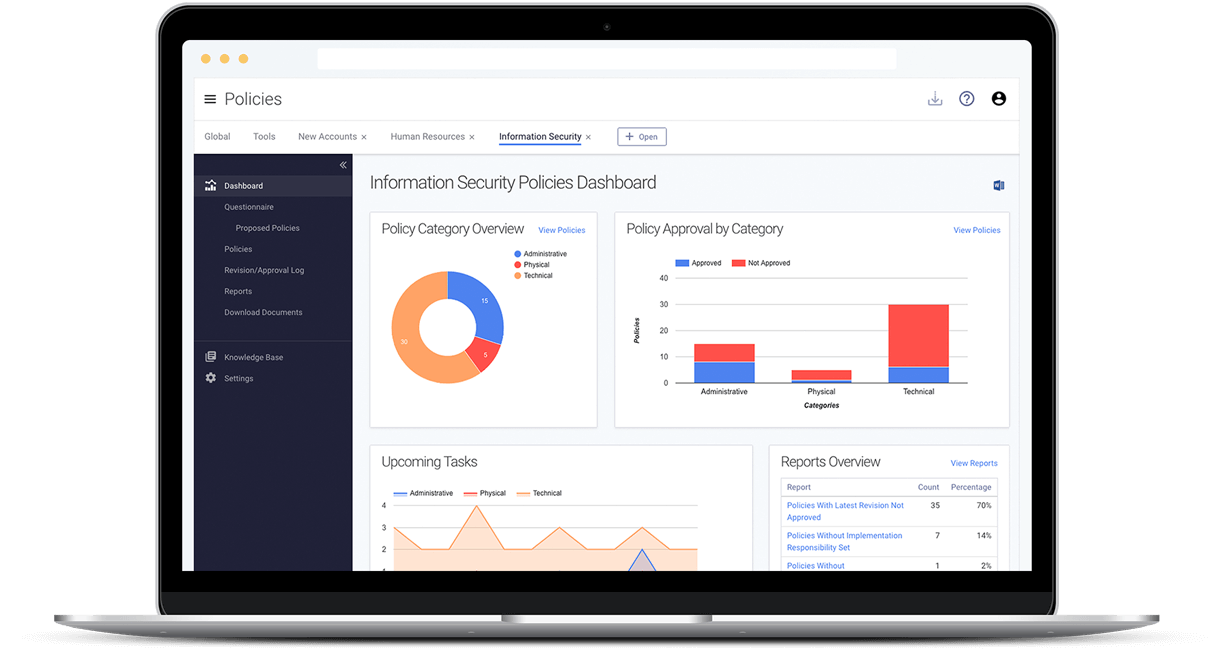
- Use global reporting to generate standardized documents
- Create an unlimited number of policies and categories
- Create tasks, assign them to users, and monitor their status
- Identify gaps with reports
- Add as many user and administrator accounts as needed
Frequently Asked Questions
Yes. Tandem provides more than 40 common information security policy templates.
The suggested policies are custom to your organization from the start, because their wording is generated from a multiple-choice questionnaire you complete. Each policy includes suggested wording, verification items, related threats and regulatory guidance.
The list of suggested policies includes:
- Change Management Policy
- Core Application Policy
- Digital Banking Policy
- Incident Management Policy
- Intrusion Detection and Prevention Policy
- IT Asset Management Policy
- Mobile Device Management (MDM) Policy
- Remote Access Policy
- Social Media Policy
- System Development Life Cycle (SDLC) Policy
- User Authentication Policy
- Vendor Management Policy
- And many more
Yes. The suggested information security policies are mapped to regulatory guidance for financial institutions (i.e., FFIEC, FDIC, OCC, FRB, and NCUA).
Additionally, Tandem allows you to optionally include references to the following standards:
- COBIT 2019
- NIST SP800-53
- PCI DSS vs. 4.0
- CIS Controls 8.1
Yes. Tandem offers a Knowledge Base with articles written by Tandem experts.
While you navigate the product you will also find help tips along the way.
Yes. Tandem Support is available 8:00 AM – 5:00 PM (CT), Monday through Friday to answer your questions about Tandem application features.
For help with the contents of your information security policies, check out our partners who can provide information security policy consulting.
You are also invited to attend our annual KEYS conference to connect with other users and learn from Tandem experts.
Tandem is pleased to offer complimentary training webinars each month for our customers. These webinars are recorded and available on-demand.
A Knowledge Base is available with articles to help you learn about Tandem. You can stay up-to-date on our latest features by subscribing to our Software Update emails.
Product training is also available by request for an additional fee.
Yes. Tandem maintains high marks through the following testing: SSAE 18 SOC 1 Type 2, internal audits and assessments, quarterly penetration tests.
Security controls include:
- Secure data transmission between your browser and your servers
- Data encrypted at rest using AES-256
- User passwords are hashed and salted
- Datacenter protected by firewall and intrusion detection/prevention systems (IDS/IPS)
- Redundant internet connections
- Multifactor authentication options
- Single Sign On (SSO) integration using SAML 2.0
- IP address restrictions
- User activity log
- User access roles/restrictions
Tandem products are delivered via the internet as Software-as-a-Service (SaaS) applications. Tandem can be accessed from any device with a modern web browser. No software installation or special equipment is required.
New features and updates are included with your annual subscription and are automatically available. Each new feature is documented in our Software Updates blog.
Yes. Tandem Policies integrate with the Tandem Information Security Risk Assessment product.
By using both modules, policies are easily mapped to threats to remain consistent with risk assessment requirements.
All Tandem products are available under the same secure website.
Yes. With a single login you can manage several companies' policies (requires a subscription for each company).