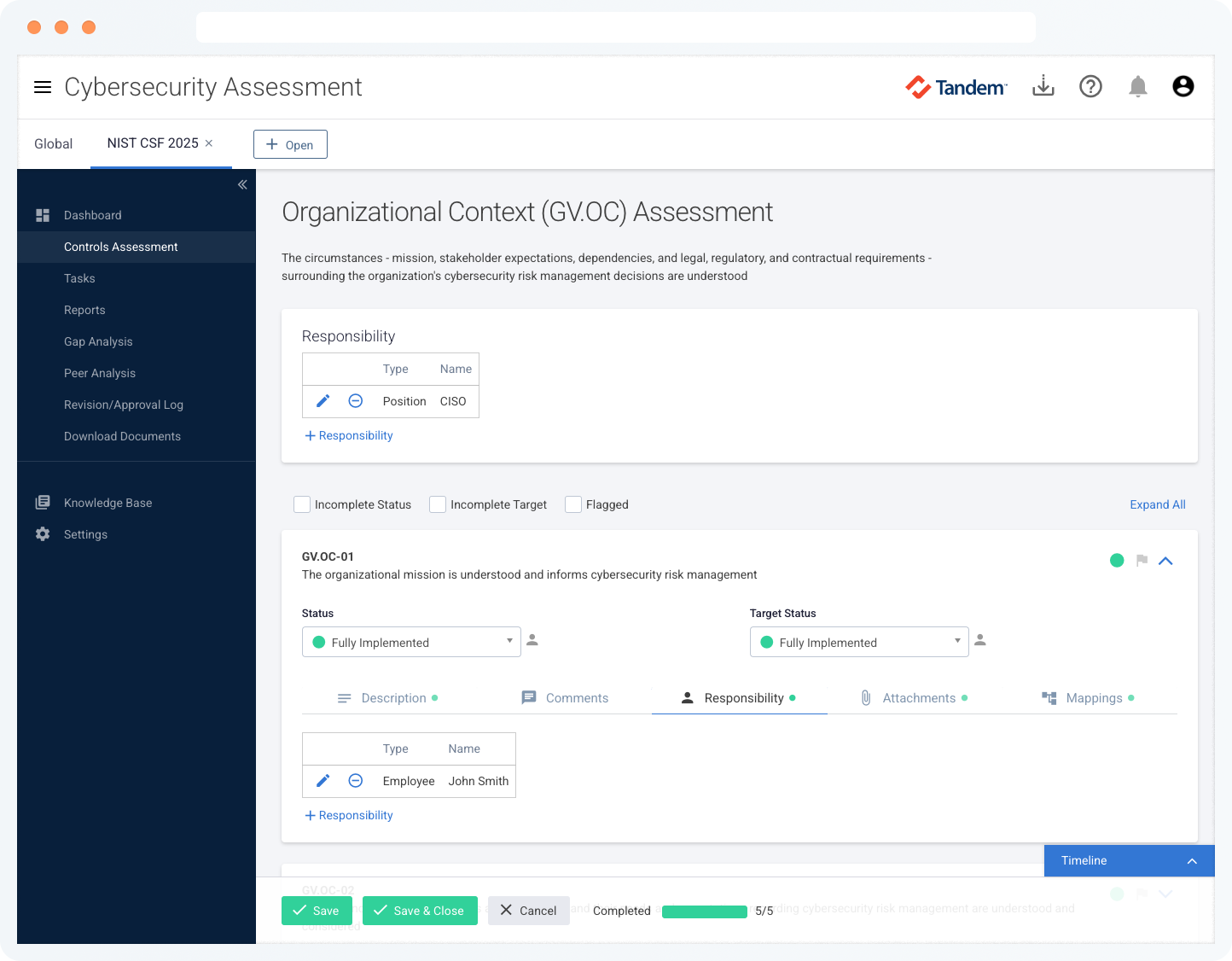
Cybersecurity Assessment
Cybersecurity Assessment
Software
Simplify your cybersecurity self-assessment process
Complete cybersecurity self-assessments in an easy, efficient, and repeatable way.
Tandem streamlines the compliance process, helping you benchmark and assess your organization's security posture against common cybersecurity control frameworks.
Frameworks
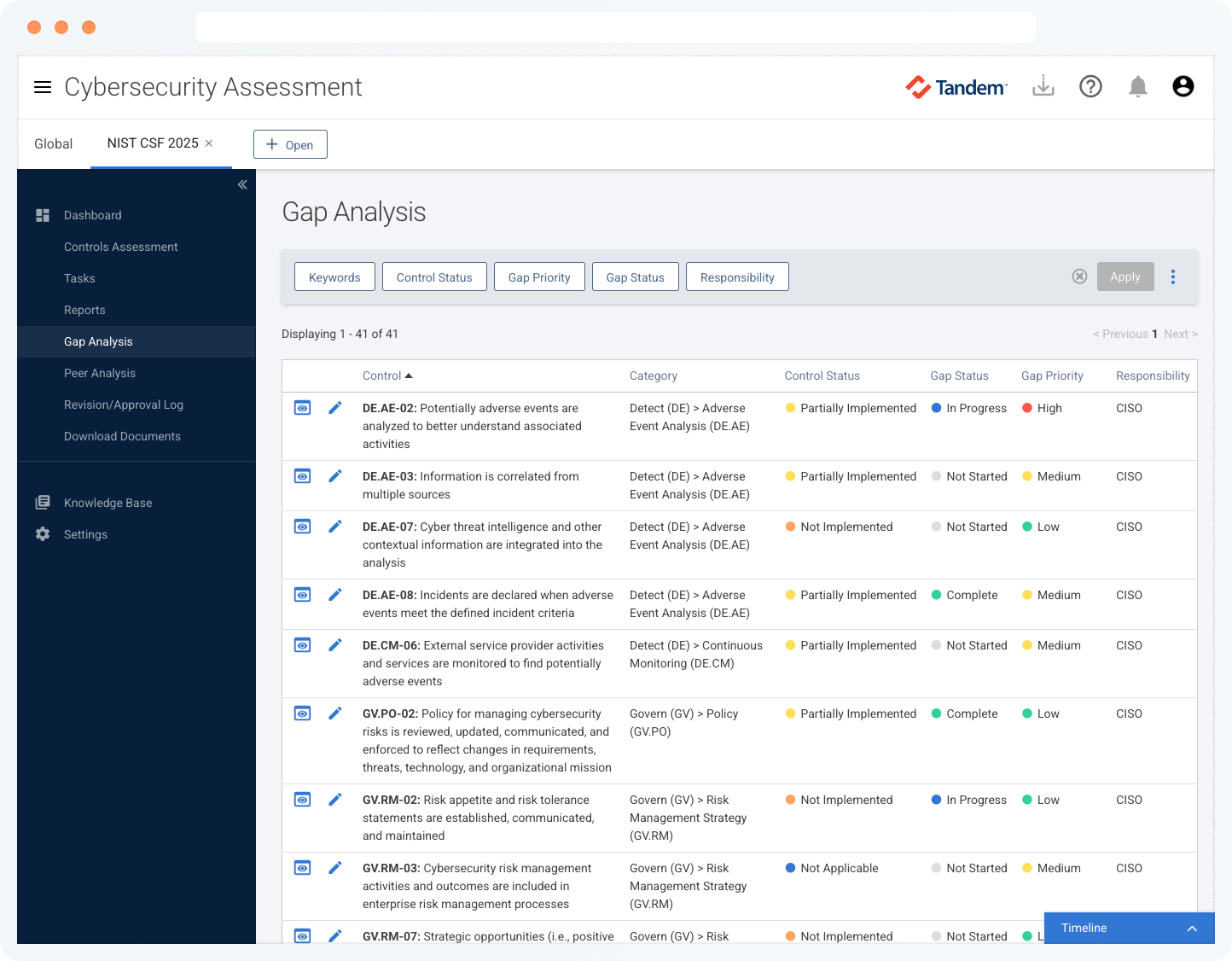
Easily complete your cybersecurity self-assessments based on frameworks like the NIST Cybersecurity Framework (CSF), CISA Cybersecurity Performance Goals (CPGs), CIS Controls, CRI Profile, and more. See the FAQ section for a full list of supported frameworks.
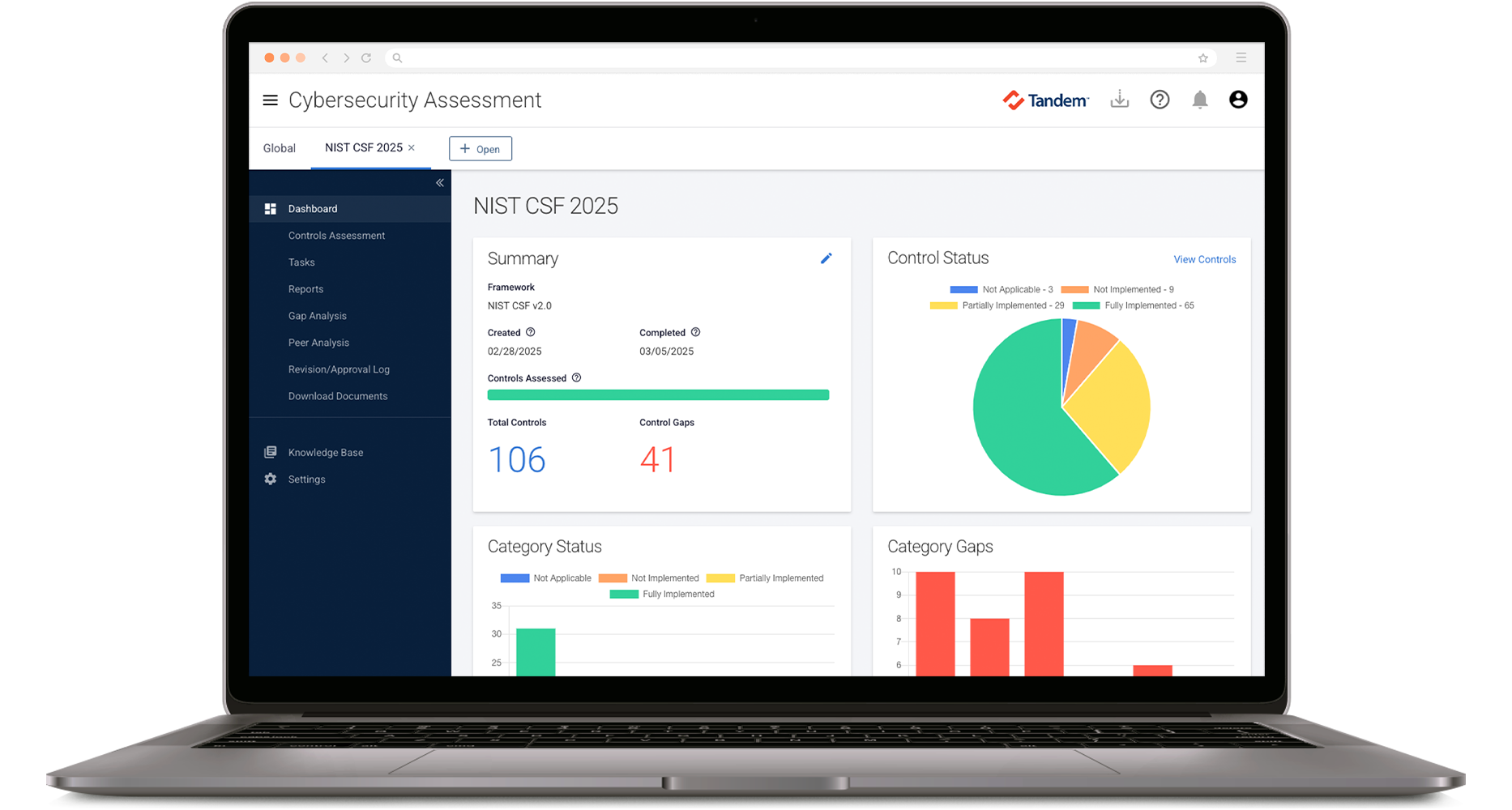
Dashboards & Reports
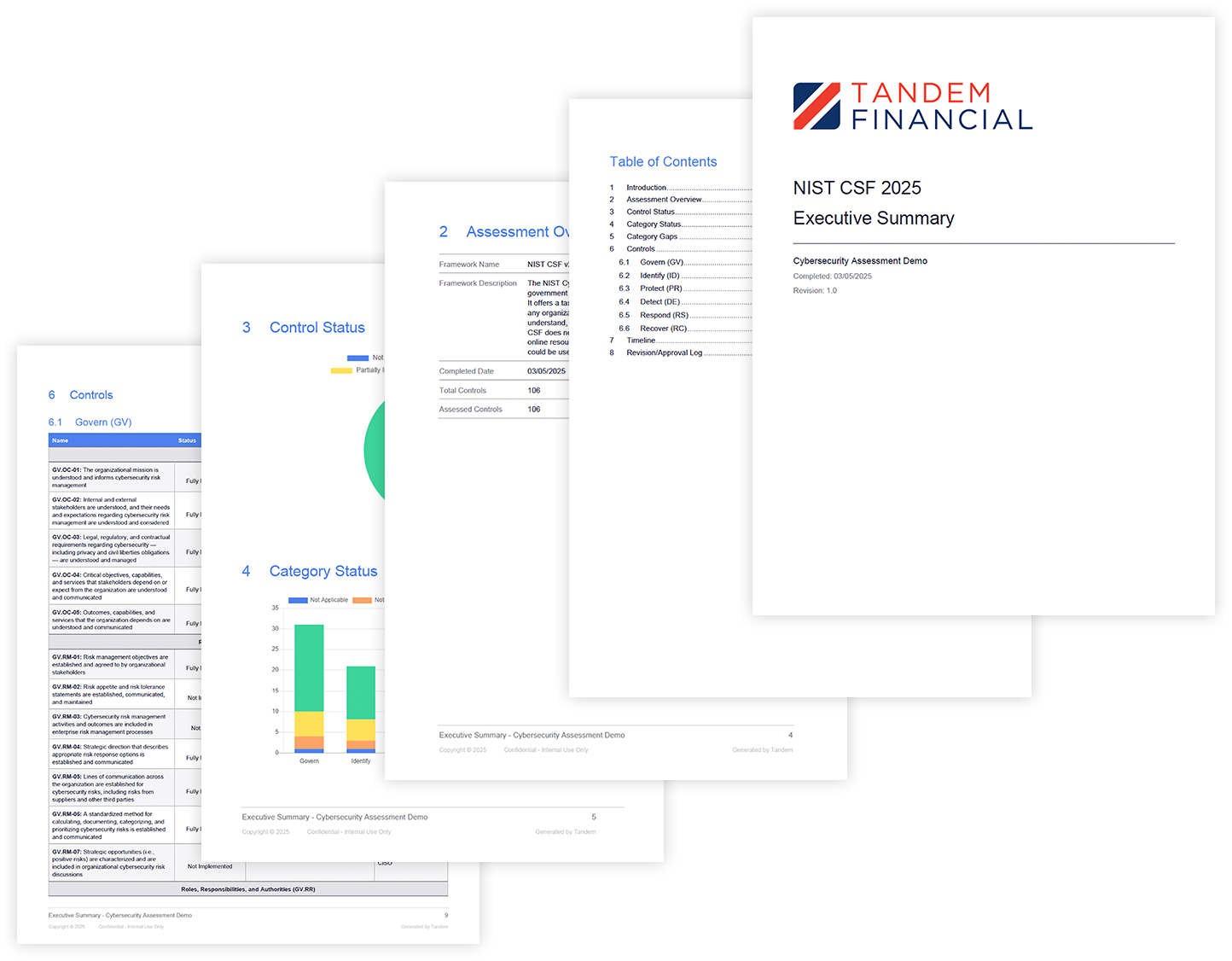
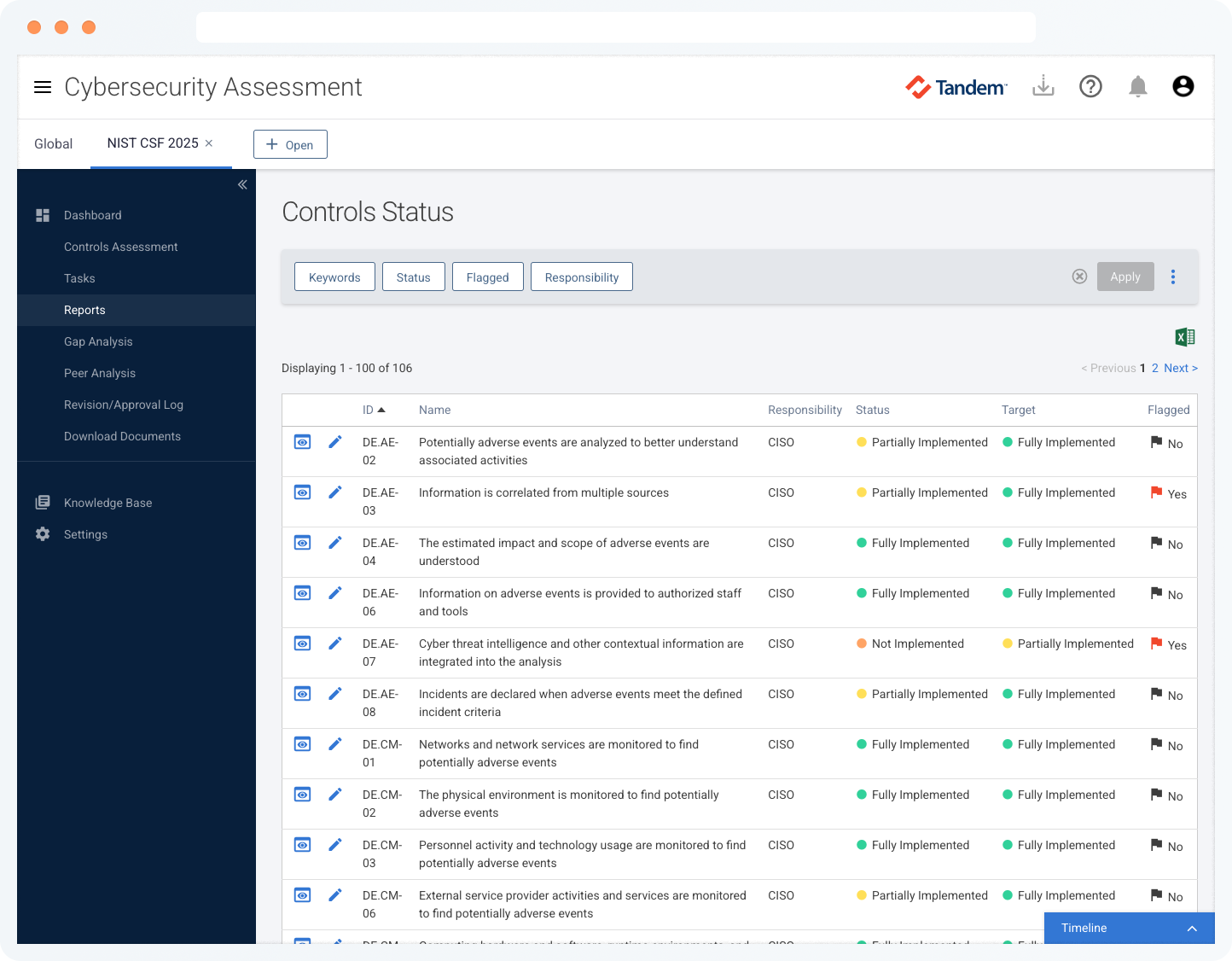
Explore clear and intuitive dashboards that give you a comprehensive snapshot of your cybersecurity assessments. Use the built-in reports to gain key insights into your control status and help ensure everything is on track.
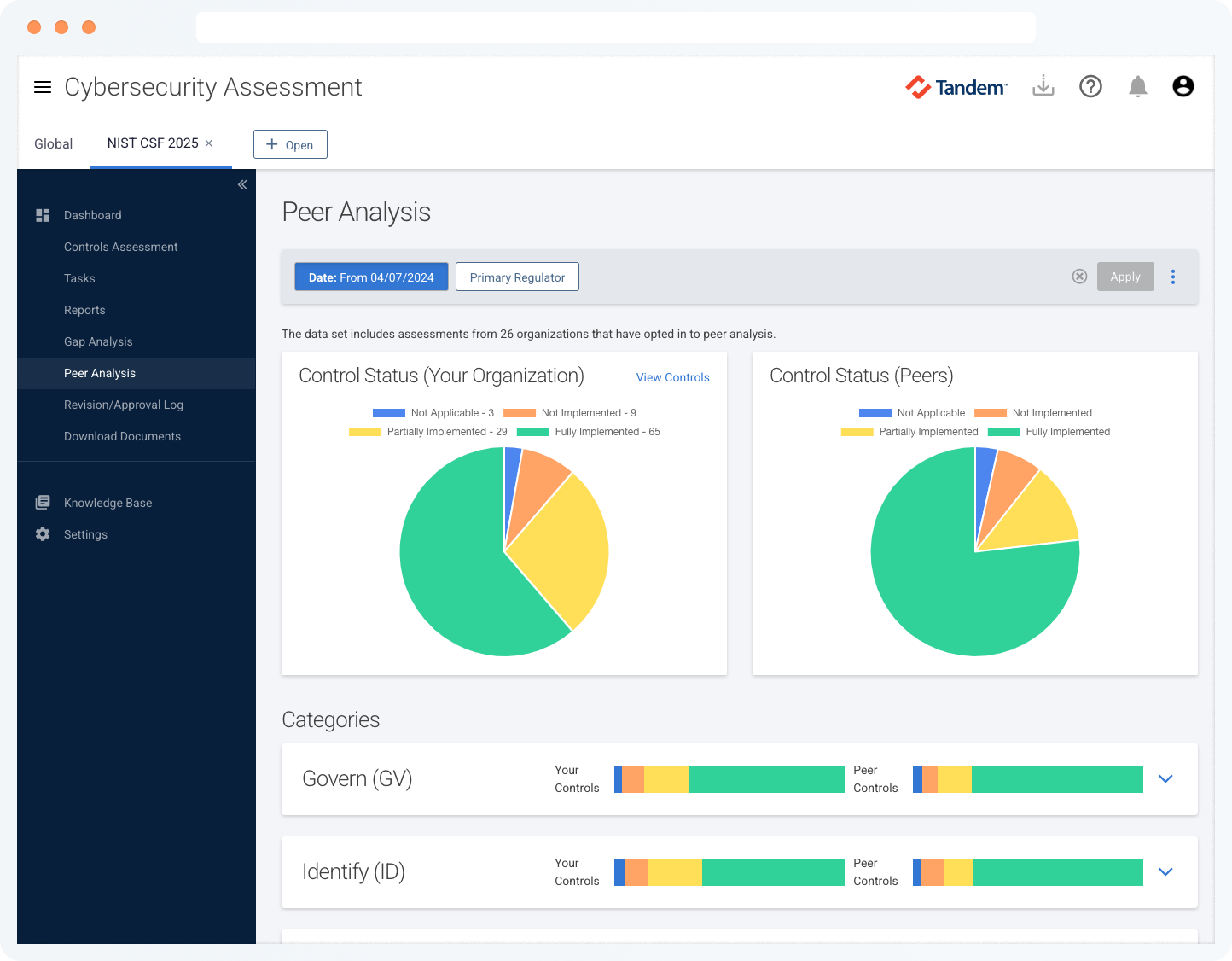
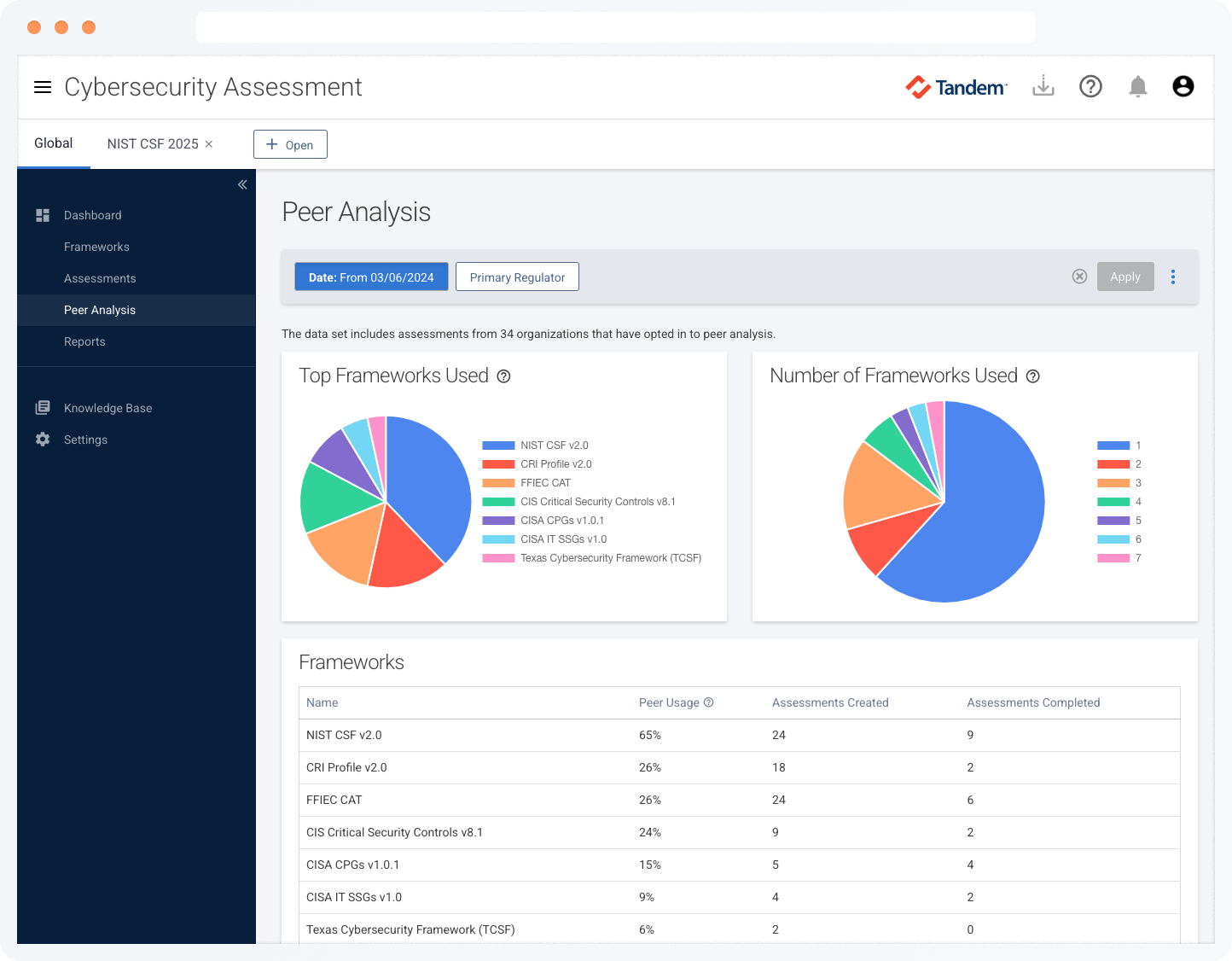
Peer Analysis
Gain perspective into your assessment results by anonymously comparing your results with more than 1,100 other organizations who have completed their cybersecurity self-assessments with Tandem.
Features |
Free
Request Access
|
Pro
Get a Quote
|
|---|---|---|
| Conduct cybersecurity assessments based on a variety of common frameworks | ||
| Set a target status for each control to help benchmark and evaluate control maturity | ||
| Create an action plan to help you respond to gaps in the assessment | ||
| Run various reports to model data in an easy-to-read format | ||
| Optionally participate in peer analysis to anonymously compare self-assessment results with other organizations | ||
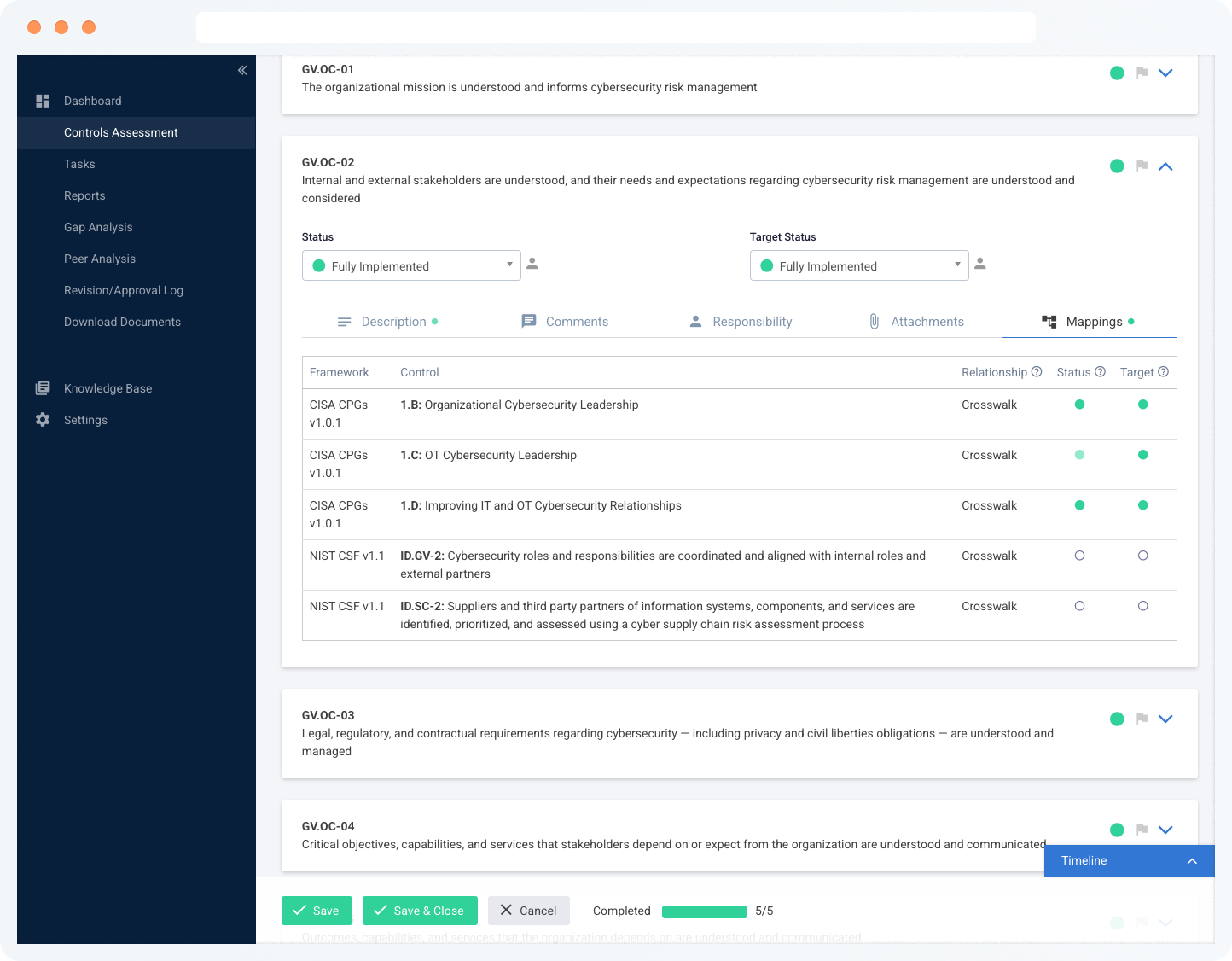
| Review industry guidance and control mappings to see cross-framework insights | ||
| Create tasks to notify self-assessment collaborators of responsibilities | ||
| Create a new assessment by copying a previously completed self-assessment | ||
| Compare self-assessment results to see improvement over time | ||
| Bulk import answers from assessments completed outside Tandem | ||
| Automatically populate control statuses from your past Tandem self-assessments using control mappings across frameworks. | ||
| Assign user access to specific categories and controls | ||
| Collaborate with your colleagues by tagging them on the automated timeline | ||
| Share your assessments securely by granting read-only access to users | ||
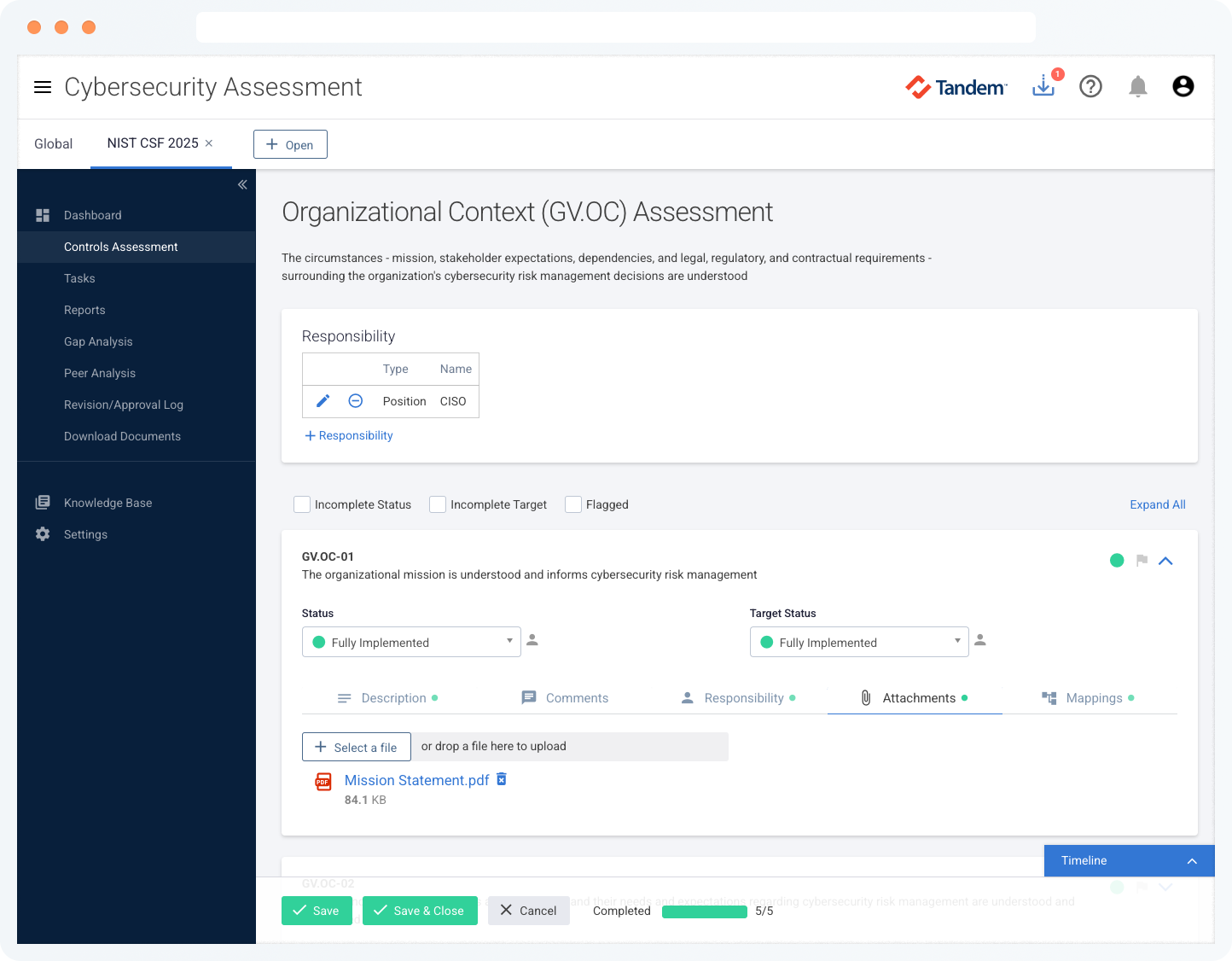
| Upload file attachments to validate control status | ||
| Create and modify custom documents to export data in presentation-ready documents | ||
| Filter peer data by regulatory body and asset size | ||
| Export peer data in easy-to-share formats | ||
| Flag controls for follow-up to ensure accuracy | ||
| Use the revision and approval log to track updates and the assessment's approval date | ||
| Create custom frameworks to expand your library of assessment templates |
Frequently Asked Questions
Template frameworks currently supported in the Tandem Cybersecurity Assessment product include:
- CIS Critical Security Controls
- CISA Cybersecurity Performance Goals (CPGs)
- CISA Health Sector-Specific Goals (SSGs)
- CISA IT Sector-Specific Goals (SSGs)
- CISA Ransomware Readiness Assessment (RRA)
- CISA Security Requirements for Restricted Transactions
- Cyber Risk Institute (CRI) Profile
- DOD Cybersecurity Maturity Model Certification (CMMC)
- DOE Cybersecurity Capability Maturity Model (C2M2)
- FDIC Information Technology Risk Examination (InTREx)
- FFIEC Cybersecurity Assessment Tool (CAT)
- FRB Operating Circular (OC) 5
- FRB Password Practice Statement (PPS)
- HHS Health Industry Cybersecurity Practices (HICP)
- HIPAA Security Rule
- NCUA Automated Cybersecurity Evaluation Toolbox (ACET)
- NCUA Information Security Examination (ISE)
- NIST AI RMF - Generative Artificial Intelligence Profile (GenAI Profile)
- NIST Artificial Intelligence Risk Management Framework (AI RMF)
- NIST Cybersecurity Framework (CSF)
- NIST Privacy Framework (PF)
- NIST SP 800-66 Rev. 2 (Implementing the HIPAA Security Rule)
- OCC Cybersecurity Supervision Work Program (CSW)
- Payment Card Industry Data Security Standard (PCI DSS)
- SAFER Guides for Health IT
- Texas Cybersecurity Framework (TCSF)
Other frameworks not included as templates may be added or imported by the user. Additional template frameworks are coming soon.
When selecting a cybersecurity framework, it can be helpful to consider factors like:
- Is the framework easy to understand?
- Is the framework easy to implement?
- Is the framework cost friendly?
- Is the framework familiar to your stakeholders (e.g., Board, examiners, etc.)?
- Is the framework easy to report?
While each financial institution’s needs and expectations may vary, understanding the extent to which a framework ticks these checkboxes is vital.
To learn more about this topic, check out our blog: What Framework Do I replace the FFIEC CAT with?
The peer analysis feature uses anonymous aggregate peer data to show how you compare with other Tandem customers in this ever-evolving cyber landscape. You can choose to include or exclude your data in the anonymous peer data set at any time.
With Cybersecurity Assessment Pro, you can filter peer results by regulatory body and asset size.
Yes. Tandem Support is available 8:00 AM – 5:00 PM (CT), Monday through Friday to answer your questions about Tandem application features.
You are also invited to attend our annual KEYS conference to connect with other users and learn from Tandem experts.
For cybersecurity consulting, check out our partners. Tandem partners can assist with item such as:
- Annual cybersecurity training for your Board of Directors
- Assistance with reporting your cybersecurity assessment results to the Board
- Consulting services, related to popular industry assessments
- Employee training on the Tandem Cybersecurity Assessment product
Tandem is pleased to offer complimentary training webinars each month for our customers. These webinars are recorded and available on-demand.
A Knowledge Base is available with articles to help you learn about Tandem. You can stay up to date on our latest features by subscribing to our Software Update emails.
Product training is also available by request for an additional fee.
Yes. Tandem maintains high marks through the following testing: SSAE 18 SOC 1 Type 2, internal audits and assessments, quarterly penetration tests.
Security controls include:
- Secure data transmission between your browser and your servers
- Data encrypted at rest using AES-256
- User passwords are hashed and salted
- Datacenter protected by firewall and intrusion detection/prevention systems (IDS/IPS)
- Redundant internet connections
- Multifactor authentication options
- Single Sign On (SSO) integration using SAML 2.0
- IP address restrictions
- User activity log
- User access roles/restrictions
Tandem products are delivered via the internet as Software-as-a-Service (SaaS) applications. Tandem can be accessed from any device with a modern web browser. No software installation or special equipment is required.
New features and updates are included with your annual subscription and are automatically available. Each new feature is documented in our Software Updates blog.
Yes. All Tandem products are available under the same secure website.
Some frameworks include references to areas of Tandem (e.g., Policies, Business Continuity Plan, Vendor Management, etc.) where the control may be addressed, if using Tandem recommended content.
Yes. With a single login you can manage several companies' cybersecurity assessments (requires a subscription for each company).