On August 29, 2024, the FFIEC announced they would be sunsetting the Cybersecurity Assessment Tool (CAT) effective August 31, 2025. For the last ten years, the CAT has been a staple for many financial institutions' cybersecurity programs. As a result, many institutions now face the question:
"Which cybersecurity framework should I use?"
If this sounds like you, you've come to the right place. While you are not expected to swap over to a new framework immediately, regulators are encouraging financial institutions to start discussing which framework to use ahead of the August 2025 deadline.
Let's talk about how to pick a cybersecurity framework.
But First, What is a Cybersecurity Framework?
Let's define a few key terms. For this article, we're defining a cybersecurity framework as a structured set of guidelines, standards, best practices, goals, and/or controls, designed to help institutions manage cybersecurity risk.
A framework can be used as the basis of a cybersecurity assessment to determine the extent to which certain framework requirements are met. Cybersecurity assessments are completed and documented using assessment tools (e.g., documents, spreadsheets, software solutions, etc.).
FFIEC CAT Alternatives
In the sunset statement, the FFIEC elected to "not endorse any particular tool." However, four frameworks were mentioned as possible alternatives to the CAT:
- The NIST Cybersecurity Framework (CSF)
- The CISA Cybersecurity Performance Goals (CPGs)
- The CRI Profile
- The CIS Controls
These four frameworks will be the focus of this article, but you may wish to consider other cybersecurity frameworks (e.g., the DoD CMMC, the DoE C2M2, the Texas Cybersecurity Framework (TCSF), PCI DSS, etc.).
The Best Cybersecurity Framework
While no single cybersecurity framework is objectively better than another, the best cybersecurity framework is one which helps you achieve your strategic goals and business objectives.
For community financial institutions, this often looks like a framework that is:
- Aligned with your size and complexity
- Easy to understand
- Easy to implement
- Cost friendly
- Familiar to stakeholders
- Easy to report
While each financial institution's needs and expectations may vary, ensuring a framework ticks these checkboxes is vital.
Before we dive into these criteria, two quick disclaimers.
- The examples provided below are my own observations. Part of the purpose of this article is to show that everyone approaches cybersecurity frameworks from different perspectives. What I see may not be how someone else sees it, and that's a good thing. So, enjoy my thoughts, but please form your own conclusions and pick a framework that works best for you. 😊
- This article may or may not apply to credit unions. The NCUA has stated that they plan to continue supporting the CAT, as it is the basis for their Automated Cybersecurity Evaluation Toolbox (ACET).
Disclaimers out of the way, let's dive into what makes a good framework.
Aligned with Your Size and Complexity
When it comes to choosing a cybersecurity framework, it really starts with a practical question: How big and complex is your organization?
Regulators aren't looking for a one-size-fits-all solution; they expect a risk-based approach that fits your specific situation.
Think about it: a $100 million credit union with a few employees isn't going to be held to the same standards as a $10 billion regional bank with dozens of business lines. Your cybersecurity strategy should grow with your organization, taking into account things like how much tech you use, what types of products and services you provide, and the overall size of your operations. So, when picking a framework, make sure it matches your footprint.
Easy to Understand
There are three qualities of a framework which makes it easy to understand: clear language, actionable steps, and a prioritized structure. Frameworks which feature practical and/or prescriptive recommendations tend to be easier to understand than others.
For example, the CISA CPGs are designed to provide clear and practical guidance. They are written in plain, non-technical language, and they are goal-oriented. This makes them easier to understand at a strategic level because they focus on what needs to be achieved, rather than prescribing how to do it.
The CIS Controls are also designed to be easy to understand. The controls guide features a "Why is this Control critical?" explanation for each control. The CIS Controls also tend to be the most prescriptive out of the four frameworks, providing concrete recommendations (e.g., 14-character passwords) as opposed to generic principles (e.g., user authentication).
In general, if you can grasp what a framework recommends and readily explain the reasoning behind it, you're on the right track.
Easy to Implement
Just because something is easy to understand doesn't mean it is easy to do. For example, it's easy to understand how to play pickleball or Call of Duty… (We're sure you can figure out where we're going with this.)
There are three framework qualities which make it easy to implement: length, flexibility, and industry relevance.
Length
Longer cybersecurity frameworks typically have a greater barrier to entry and they are more challenging to maintain. One of the biggest challenges of the FFIEC CAT was its length, coming in at a grand total of 494 declarative statements.
Some good news: Each of the four frameworks listed above is shorter than the FFIEC CAT.
- The CISA CPGs have 38 security practices.
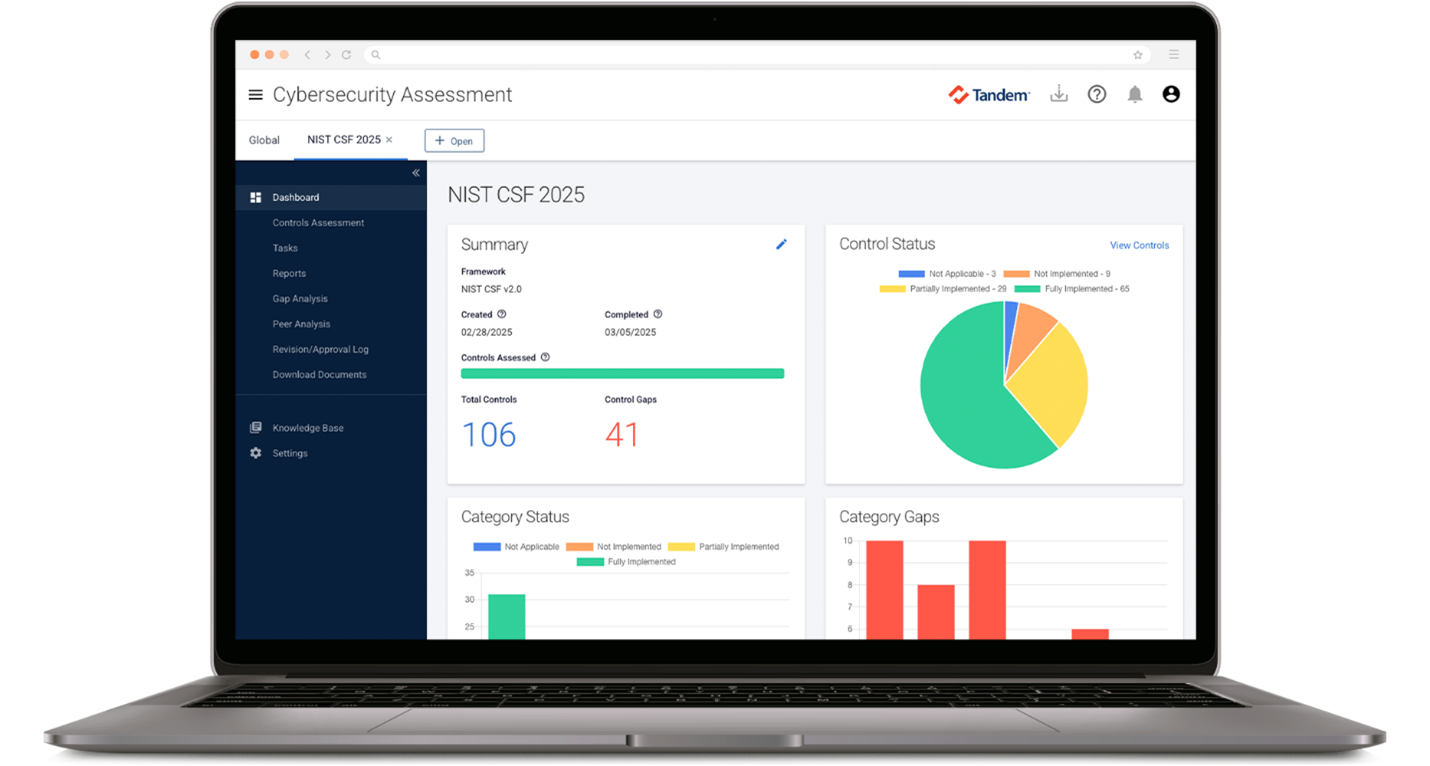
- The NIST CSF has 106 outcomes.
- The CIS Controls have (up to) 153 safeguards.
- The CRI Profile has (up to) 318 diagnostic statements.
The CIS Controls and CRI Profile both feature target maturity levels. The CIS Controls call them "Implementation Groups" and the CRI Profile calls them "Tiers." The maturity levels are designed to provide a roadmap for users to start smaller and improve their maturity over time. At the lowest level of maturity, the CIS Controls have 56 safeguards and the CRI Profile has 208 diagnostic statements.
In short, longer frameworks aren't bad, but they may involve more people, time, and structure.
Flexibility
Controls rarely exist in a "Yes" or "No" state. This was another common challenge associated with the FFIEC CAT. While the CAT was updated in 2017 to add a "Yes, with compensating controls" option, the other frameworks tend to be more flexible.
For example:
- The CISA CPGs allow users to state whether a security practice is "Implemented," "In Progress," "Scoped," or "Not Started."
- The CRI Profile spreadsheet allows users to select from the following: "Yes," "No," "Partial," "Not Applicable," "Yes – Risk Based," "Yes – Compensating Control," "Not Tested," "I Don't Know," and "To Be Assessed."
- The NIST CSF and CIS Controls do not provide recommended answer options, so it is ultimately up to the user to decide how they wish to classify the control status (e.g., Not Applicable, Not Implemented, Partially Implemented, Fully Implemented, etc.).
Industry Relevance
One of the biggest selling points of the CAT is that it was designed for financial institutions by the federal regulators. This helped promote compliance with existing regulations and guidance.
To that end, the only framework currently created specifically for use by financial institutions is the CRI Profile.
CISA is also working with the Department of the Treasury (the Sector Risk Management Agency for the financial services sector) to develop financial institution-specific CPGs. Based on what we know of other sector-specific CPGs, we anticipate the financial version will map the CPGs to relevant regulation and guidance.
While the other control frameworks are industry agnostic, there are mapping tools available which can help users connect the dots, such as the OCC's Cybersecurity Supervision Work Program References tool and Tandem's upcoming support for multiple framework assessments.
Cost Friendly
While each of the frameworks are free for financial institution use, there are still costs to consider, including control costs, time costs, and vendor costs.
- Control costs include the costs associated with implementing the best practices or controls recommended by the framework. The more prescriptive the controls, the more costly it may be to achieve compliance. For example, if a framework requires you to implement specific technical controls (e.g., application allowlisting, data loss prevention (DLP) tools, single sign on (SSO), etc.), there may be costs associated with implementing that specific control.
- Time costs include the amount of time it will take to adopt and complete a framework assessment. When assessing time costs, consider not only the length and complexity of the assessment, but also the number of people involved with the project and how much time it would take year-over-year to update.
- Vendor costs include the costs associated with using consulting services or software tools to complete a framework assessment. Government-developed, public domain frameworks (i.e., the NIST CSF or CISA CPGs) are easier and less expensive for vendors (e.g., your MSP, auditors, consultants, etc.) to support than proprietary frameworks, which have strict licensing arrangements and commercial use restrictions.
Make sure you choose a framework that gives you the most value without draining your resources.
Familiar to Stakeholders
Another factor to consider is familiarity to stakeholders. For this concept, the term "stakeholder" includes Board members, examiners, auditors, consultants, and other employees of your institution.
While each of these four frameworks may be at least somewhat familiar to your stakeholders, there is one which stands out more than the others.
The NIST CSF is the OG of cybersecurity frameworks. It has the greatest name recognition of the four. The NIST CSF is so popular, other frameworks base their control groupings on the NIST CSF functions (i.e., Govern, Identify, Protect, Detect, Respond, and Recover). It is also used as the foundation for some of the federal regulators' examination work programs, such as the OCC's Cybersecurity Supervision Work Program. NIST also helped with the development of the FFIEC CAT, reviewing and providing input on the CAT's Appendix B: Mapping Cybersecurity Assessment Tool to the NIST Cybersecurity Framework.
According to data from Tandem's 2024 Cybersecurity Report for the Financial Institution Industry, the NIST CSF already has a reported adoption rate of 70%, almost three times more than the next reported framework, the CIS Controls, at 24%. It should be noted, the CISA CPGs are relatively new, but have still seen a noticeable adoption in the financial sector (9%) since their release in October 2022.
In a more recent webinar hosted by Tandem, we asked attendees which frameworks they were considering as a replacement for the FFIEC CAT. Here's what we found out from the 365 attendees who participated in the survey:
- NIST CSF: 73%
- CRI Profile: 27%
- CIS Controls: 27%
- CISA CPGs: 24%
- Other: 3%
With those stats in mind, it looks like interest in all four frameworks is increasing, which means increased familiarity too.
Familiarity is important because it means there's less of a learning curve for your stakeholders.
Easy to Report
Going hand-in-hand with several of the previous considerations, you want to pick a framework that is easy to report. Frameworks which are easier to understand and implement (e.g., smaller, less technical, etc.) also tend to be easier for stakeholders to understand than others.
If you are planning to use a software tool, like Tandem, to help you document and track your cybersecurity assessments, the product should include:
- Summary reports to help you present your framework assessment results in a meaningful manner.
- Executive-level data, so senior management can quickly see what's working and what needs attention.
-
Charts and graphs because pictures speak louder than bullet points.
Find a way to track your progress, pull clean reports, and share updates without having to build everything from scratch.
Next Steps
Each of the frameworks mentioned in the FFIEC statement have distinct advantages. At the end of the day, the best cybersecurity framework is the one which best supports you and your business.
If you're looking for next steps, check out Tandem's quiz on Which Cybersecurity Framework is the best fit for you? This quiz looks at your organization's size, complexity, risk, and preferences. At the end, you'll get a ranked list of the four frameworks, plus a fun little breakdown of how your answers shaped the result.
If you know which framework you're going to use and you're ready to get started, check out Tandem Cybersecurity Assessment. Learn more and sign up for the free version at Tandem.App/Cybersecurity.