On February 26, 2024, the National Institute of Standards and Technology (NIST) published an update to their Cybersecurity Framework (CSF). A decade since the framework made its first appearance, the NIST CSF 2.0 includes several significant changes. In this article, we'll cover six of those key updates and talk about what it means for you.
#1. A New Name
In February 2013, Executive Order 13636 appointed NIST to develop a "framework to reduce cyber risks to critical infrastructure." As a result, this is pretty much what NIST called the first version of the document: "Framework for Improving Critical Infrastructure Cybersecurity."
Even though the name rolls right off the tongue, nobody called it that. Both NIST and the industry regularly referred to it as the "Cybersecurity Framework."
So, with this update, NIST made it official. Version 2.0 is now called "The NIST Cybersecurity Framework (CSF) 2.0."
#2. A Broader Focus
The title isn't the only place NIST got rid of the "critical infrastructure" concept. The previous version of the framework referred to critical infrastructure more than 40 times.
Excluding the one instance where NIST told people about the name change, the CSF 2.0 doesn't talk about critical infrastructure at all.
In their press release, NIST said the reason for this change is the CSF "now explicitly aims to help all organizations – not just those in critical infrastructure, its original target audience – to manage and reduce risks."
So, if you haven't completed the CSF because it was for "critical infrastructure," now you can!
#3. A Heart for Governance
The prior version of the CSF had five functions: Identify, Protect, Detect, Respond, and Recover. While several of the functions touched on concepts related to cybersecurity governance, NIST looked at the framework and said, "Ehhh, it's not enough."
As a result, a new function was added to the framework called "Govern." In the CSF 2.0 infographic, the new function connects to and sits smack dab in the middle of the five other functions, showcasing the idea that effective governance carries the team harder than LeBron James has carried every team he's ever played with.
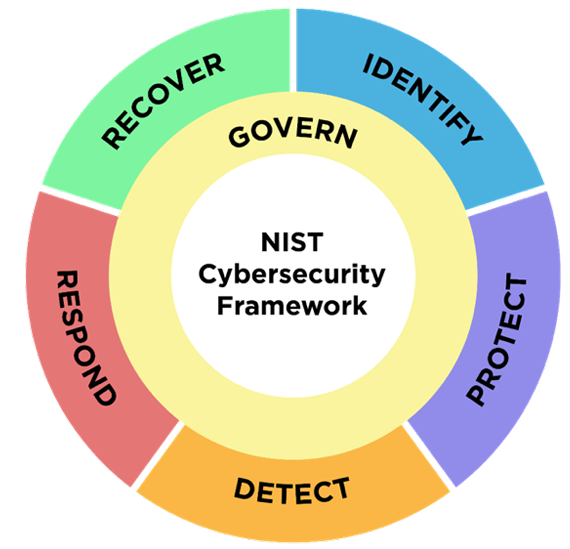 In the press release, NIST defines governance as "how organizations make and carry out informed decisions on cybersecurity strategy." What this means is that it is important for leaders in organizations to take an active role in helping identify and mitigate cyber risk.
In the press release, NIST defines governance as "how organizations make and carry out informed decisions on cybersecurity strategy." What this means is that it is important for leaders in organizations to take an active role in helping identify and mitigate cyber risk.
While some of the categories and subcategories in the Govern function are entirely new, several come nearly verbatim from the previous version.
|
|
Version 1.1 |
Version 2.0 |
|
Category Example |
Risk Management Strategy (ID.RM) The organization's priorities, constraints, risk tolerances, and assumptions are established and used to support operational risk decisions.
|
Risk Management Strategy (GV.RM) The organization's priorities, constraints, risk tolerance and appetite statements, and assumptions are established, communicated, and used to support operational risk decisions. |
|
Subcategory Example |
ID.AM-6 |
GV.SC-02 Cybersecurity roles and responsibilities for suppliers, customers, and partners are established, communicated, and coordinated internally and externally |
In short, cybersecurity risk is an enterprise risk, so organization leadership needs to take center stage in managing it.
#4. A Stronger Supply Chain
As third-party risk continues to increase, it makes sense NIST would want to level up the CSF in this area. Some of the fresh faces you can expect to see in the CSF 2.0 include:
- GV.SC-04: Knowing and prioritizing suppliers by criticality.
- GV.SC-06: Performing planning and due diligence before entering third-party relationships.
- GV.SC-09: Integrating supply chain security practices into the bigger (cybersecurity) picture.
- GV.SC-10: Planning for termination of the relationship.
If these things sound like core components of a vendor management program, that's because they are. Vendor management is not just something to do for compliance purposes. When done correctly, it can be a true value-add for your cybersecurity risk management program.
#5. A Focus on Improvement
Just like the CSF, cybersecurity is not a "once and done" kind of thing. It grows. It changes. It improves. (Or at least it should.) Because of this, the CSF 2.0 places a lot of new emphasis on continuous improvement. For example:
- A new Oversight (GV.OV) category was added. It says, "Results of organization-wide cybersecurity risk management activities and performance are used to inform, improve, and adjust the risk management strategy."
- A new Improvement (ID.IM) category was added. It says, "Improvements to organizational cybersecurity risk management processes, procedures and activities are identified across all CSF Functions." (Previously, there were "Improvements" categories in the Respond and Recover functions, but they focused on improving those specific aspects of the plan, as opposed to the plan as a whole.)
In other words, continually work to level up your plan. You'll thank yourself later.
#6. A Lot of Helpful Resources
NIST went above and beyond with the CSF 2.0. In addition to the framework itself, NIST also published several resources, designed to make using the tool easier, including:
- Quick Start Guides to help you get familiar with the tool, like this one for small businesses.
- CSF Profile Templates to help you identify any gaps between your current and target state.
- Implementation Examples to help you understand what the CSF 2.0 subcategories mean.
- Informative References (Mappings) to help you connect CSF 2.0 concepts to existing assessment tools, control libraries, and frameworks.
Next Steps
If you are looking for your next steps for the NIST CSF 2.0, here's what we'd like to recommend:
- Download the CSF 2.0. Read through it for yourself and get familiar with the updated functions, categories, and subcategories. Learn more.
- Check out the Resources. The implementation examples are especially helpful for learning about practical ways the CSF 2.0 may be implemented. Learn more.
- Download the Tandem Mapping. If you use Tandem, check out the "Tandem Mapping: NIST Cybersecurity Framework 2.0" on the Resources page. This resource serves to identify areas of Tandem where NIST CSF 2.0 references are (or could be) addressed. If you don't use Tandem, then find out how Tandem's GRC software can help you to comply with NIST and other regulatory guidance and frameworks at https://tandem.app.
To wrap it up, the CSF 2.0 is a significant improvement on the former versions of the NIST Cybersecurity Framework. When implemented, it can give you the tools and terminology you need to stay strong and continue improving the cybersecurity of your organization.



