On April 3, 2025, the National Institute of Standards and Technology (NIST) released SP 800-61 Rev. 3, a new guide covering Incident Response Recommendations and Considerations for Cybersecurity Risk Management. This update supersedes SP 800-61 Rev. 2, also known as the Computer Security Incident Handling Guide. But what does that mean exactly?
Let's dive into what's new and what it means for your incident response plans.
About the Guidance
At first glance, it might seem like NIST tossed out the old guidance and rewrote everything from scratch. I'm here to tell you… That's pretty much exactly what happened.
NIST SP 800-61 Rev. 3 has been completely restructured to align with the NIST Cybersecurity Framework (CSF) 2.0 with the goal of better integrating incident response into broader risk management activities.
The CSF-aligned structure brings a lot of advantages. Rev. 3 is more flexible, more scalable, and better suited for today's complex, fast-moving, and highly outsourced environments. It speaks to a world where incident response isn't just a technical activity; it's a critical function of an organization's overall security strategy.
That said, some readers (hi, it's me 👋) might miss the more straightforward, narrative style of Rev. 2. The previous version walked incident handlers step-by-step through each stage in a way that just made sense. For teams used to that flow, Rev. 3's framework-first format can feel a little disjointed.
While Rev. 2 may be (definitely) showing its age, it still stands out as one of the more practical, hands-on guides out there. It's full of real-world examples and explanations that still resonate. So, don't recycle your old copy just yet, especially if you're new to incident response theory. It still has a lot to offer. 🌱
Simplified Stages
Disclaimers aside, one of the best (and most notable) changes in Rev. 3 was the streamlining of the incident response lifecycle. If you're familiar with Rev. 2 (or if you've read any of our blogs over the last five years), you've probably seen the six stages at some point or another.
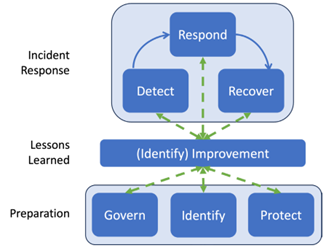
Rev. 3 consolidates the stages into the NIST CSF functions like this.
| Revision 2 (Before) | Revision 3 (After) |
| Detection | Detect |
| Analysis | |
| Containment | Respond |
| Eradication | |
| Recovery | Recover |
| Post-Incident Activity | Improve |
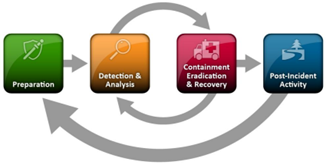
If you're more of a visual person, below are the old and new illustrations NIST used to model the incident response life cycle process.
| Revision 2 (Before) | Revision 3 (After) |
 |
 |
One more change in Rev. 3 is that the "Improve" stage isn't just about holding a lessons learned meeting at the end of incident response (i.e., "Post-Incident Activity") anymore. This update reflects a focus on continuous improvement throughout the entire incident lifecycle.
In short, don't wait to improve if there's something you can do better right now. That's just good life advice. 💯
Guidance Structure
As I've already mentioned, another big change in this latest revision isn't just what it says, but how it's organized.
- Rev. 2 walked you through the incident response lifecycle stage-by-stage (i.e., Detection, Analysis, Containment, Eradication, Recovery, and Post-Incident Activity). It was written like a playbook for responders.
- Rev. 3 is structured around the NIST CSF, using the function, category, and subcategory model (e.g., DE, DE.CM, DE.CM-01). It is written more like a best practices guide for management.
Each CSF element in Rev. 3 includes:
- Recommendations (R): What the organization should do.
- Considerations (C): What the organization may need to think about.
- Notes (N): Additional background, caveats, or references to other guidance.
This structural shift reflects a broader change in mindset, from tactical execution to strategic alignment. Rev. 3 is less of a hands-on how-to guide and more of a framework for making sure your incident response activities support your organization's broader objectives, cybersecurity and otherwise.
This is a big win in some ways, but if you work for a smaller organization and you're looking for boots-on-the-ground guidance, it might leave you wanting more. 🥾
Let's Compare a Few Topics
Incident Detection
In Rev. 2, detection was explained largely through examples. It walked readers through what to look for and where to look, with a focus on:
- Attack vectors (e.g., removable media, phishing emails, stolen devices)
- Signs of an incident (e.g., suspicious log entries, antivirus alerts, unusual network traffic)
- Sources of precursors and indicators (e.g., system alerts, logs, user reports)
Rev. 3 reframes detection within the Detect function of the CSF, especially through the Continuous Monitoring category (DE.CM). Instead of focusing on possible signs of an incident, Rev. 3 encourages organizations to ask: "What do we monitor, and why?"
The guidance now recommends monitoring a broad range of sources, including assets, networks, personnel activity, technology usage, service providers, and the physical environment.
Incident Analysis
In Rev. 2, incident analysis was all about digging through logs, correlating alerts, and using all available resources to confirm if something suspicious was actually an incident. It focused heavily on technical investigation, covering topics like log retention, packet sniffers, and even using "internet search engines for research." (I told you it was old. 😅)
Rev. 3 shifts focus to the Anomalies and Events (DE.AE) and Incident Analysis (RS.AN) categories of the CSF. Now, the emphasis is on building a smarter, more efficient process for analyzing potentially adverse events. Some key takeaways from the new guidance include:
- Integrating cyber threat intelligence (CTI) to better understand incidents
- Implementing SIEM and SOAR systems to reduce noise and prioritize resources
- Automating alerts, ticketing, and information sharing
- Declaring incidents based on defined criteria, balancing risk and false positives
If some of these practices seem advanced, it's because in many ways they are. Rev. 3 acknowledges the volume of data organizations face in 2025 is simply too much for humans to analyze alone, and it encourages using modern technology to bridge the gap. The challenge, of course, is not every organization has the budget or capacity for those tools yet.
If this sounds like your situation, the first step is to recognize your current state, make steady progress where you can, and use guidance like this to help strengthen your case for additional resources.
Incident Communication Guidelines
In Rev. 2, incident communication was mostly about making sure the right people knew what was going on. The guidance gave a pretty clear list of people to notify, including your CIO, security team, legal, HR, and law enforcement. It also talked about ways to get the word out, like calling people, posting paper notices, updating voicemail greetings, sending telegrams... (Okay, maybe not that last one. 📬)
Rev. 3 takes things a step further. Instead of focusing on who to tell, it treats communication as part of a broader coordination effort. It now includes things like:
- Defining the difference between escalation and elevation
- Notifying customers and regulators, when needed
- Managing media inquiries
- Proactively sharing threat information with trusted partners
- Complying with ever-evolving incident reporting regulations
Takeaways
Honestly, it's kind of challenging to compare NIST SP 800-61 Rev. 2 and Rev. 3 because even though they approach the same incident response topics, they do so from very different points of view. Rev. 3 no longer features a lot of the tangible recommendations which were so prevalent in Rev. 2, yet Rev. 2 is missing a lot of modern concepts and terminology explored in Rev. 3.
In short, even though Rev. 3 is the latest iteration of the guidance, both documents provide helpful recommendations on managing and responding to incidents in their own ways.
Additional Guidance
While NIST SP 800-61 is considered foundational incident response guidance, it is not the only incident response guidance. One thing Rev. 3 does well is point readers to additional sources of information, many of which have been released or updated since Rev. 2's publication date.
Some of the sources include:
- NIST SP 800-84 Guide to Test, Training, and Exercise Programs for IT Plans and Capabilities
- NIST SP 800-92 Guide to Computer Security Log Management
- NIST SP 800-150 Guide to Cyber Threat Information Sharing
- NIST SP 800-184 Guide for Cybersecurity Event Recovery
- NIST SP 800-216 Recommendations for Federal Vulnerability Disclosure Guidelines
While I wouldn't call these "required summer reading" by any means, especially for small to midsize organizations, they can be helpful if you want to tuck them away for a rainy day. ☔
Next Steps
Whenever new guidance drops, it's a great opportunity to step back and look at your incident response process from a fresh perspective. If you're wondering where to start, here are a few suggestions.
- Download a copy of NIST SP 800-61 Rev. 3 and get familiar with the updated structure.
- Perform a cybersecurity self-assessment using the NIST CSF. Many elements in Rev. 3 align directly with CSF elements which can make it easier to evaluate your incident response capabilities.
- Use the recommendations and considerations in Rev. 3 to guide both your assessment and review of your current incident response plan, but be prepared to do some interpreting, application, and gap analysis.
The good news? Since the new guidance generally focuses more on theoretical processes than prescriptive steps, you're probably closer to alignment than you think. 💡
How Tandem Can Help
Tandem is a suite of GRC software applications designed to help organizations improve their cybersecurity risk management and incident response capabilities.
- Tandem Incident Management is designed to help you build your incident response plan and track incidents when they occur. When new guidance is released, we update our software and template content to ensure it reflects the latest recommendations with industry best practices for incident response. Learn more at Tandem.App/Incident-Management-Software.
If you currently subscribe to the product, check out our software update blog about changes we've made in response to the guidance. ✅
- Also, Tandem Cybersecurity Assessment allows you to conduct cybersecurity self-assessments based on common frameworks, including the NIST CSF. Sign up for free to get started on your first CSF assessment at Tandem.App/Cybersecurity.
Learn more at Tandem.App or Watch a Demo to see these products in action.