The FFIEC Cybersecurity Assessment Tool, known also as the "CAT," has a rich history. A decade since the CAT's foundations were first put into place, the question must now be asked: What's next? Will the CAT be updated? Will the CAT be replaced? While we can't predict the future, here are six factors which may influence what's next for the FFIEC CAT.
1. The CAT's Current Content
The first factor we need to talk about is the current content of the FFIEC CAT. The CAT's content has existed in its current form since it was originally published in June 2015.
Since that time, the FFIEC has released the following updates to the IT Examination Handbook:
- FFIEC Management Booklet (November 2015)
- FFIEC Retail Payment Systems Booklet (April 2016)
- FFIEC Information Security Booklet (September 2016)
- FFIEC Business Continuity Management Booklet (November 2019)
- FFIEC Architecture, Infrastructure, and Operations Booklet (June 2021)
Additionally, the FFIEC has released standalone guidance documents on relevant security topics, including:
- Cyber Attacks Involving Extortion (November 2015)
- Cyber Insurance (April 2018)
- Security in a Cloud Computing Environment (April 2020)
- Authentication and Access to Financial Institution Services and Systems (August 2021)
In reviewing these guidance documents, some topics the CAT does not explicitly address would include:
- Personally owned devices (a.k.a., "bring your own device" or "BYOD")
- Cloud computing solutions (e.g., file exchange and sharing, cloud hosting, etc.)
- Application programming interfaces (APIs)
In addition, while the concepts might be addressed, the CAT is missing certain keywords which have become familiar in the industry (e.g., identity and access management (IAM), data identification, shadow IT, telework, etc.).
Finally, some recommendations which were considered "Evolving" or "Intermediate" in 2015 would now be considered "Baseline." For example, the following items are expected from the NCUA's new Information Security Examination (ISE) program.
|
FFIEC CAT Statement |
ISE Statement |
|
Employment candidates, contractors, and third parties are subject to background verification […] (Evolving) |
The information security training program includes […] new employee training and background checks. (SCUEP & CORE) |
|
Antivirus and anti-malware tools are updated automatically. (Evolving) |
Anti-virus/Anti-Malware controls include the following: Workstations/Servers receive automatic updates. (CORE) |
|
Baseline configurations cannot be altered without a formal change request, documented approval, and an assessment of security implications. (Intermediate) |
[The change management process includes] Procedures to document requests and approvals. (CORE) |
What This Means: While the FFIEC CAT remains one of the most comprehensive and widely used cybersecurity control assessments by financial institutions, there are key topics, terminology, and best practices that have been adopted as baseline controls by the industry since 2015.
2. NIST Cybersecurity Framework
Another factor we need to recognize is that the FFIEC CAT was based on the NIST Cybersecurity Framework (CSF). The NIST CSF has had its own journey, and is currently in the process of a major update.
Historically speaking, one of the FFIEC's goals has been to provide guidance and resources tailored for the financial sector which are consistent with federal standards, requirements, and best practices, such as those provided by NIST.
What This Means: If the CAT (1.0) was based on the NIST CSF (1.0), it would stand to reason that the federal banking agencies would wait to release CAT (2.0) until NIST CSF (2.0) is finalized.
3. Agency Examination Programs
A third factor in this conversation is how the individual FFIEC member agencies are using the CAT as part of their exams. For example:
- FDIC Information Technology Risk Examination (InTREx) Program
The InTREx Program was released in 2016 and continues to be used by the FDIC, Federal Reserve, and several state banking agencies. While the program states financial institutions are not required to use the CAT to assess cybersecurity preparedness, the program also states that examiners would reference the CAT's Appendix A when performing exams. That said, InTREx is currently under review and is expected to be updated in the near future, according to the FDIC's 2023 Report on Cybersecurity and Resilience. - NCUA Automated Cybersecurity Examination Tool (ACET)
From 2018 – 2020, the NCUA piloted an examination program called the Automated Cybersecurity Examination Tool (ACET). The ACET was based on the FFIEC CAT. While the ACET has been replaced as an exam program, the NCUA continues to encourage credit unions to conduct "voluntary, cybersecurity self-assessments" and may use the NCUA ACET / FFIEC CAT as one way to accomplish this. Learn more about this topic in the Tandem Blog: Credit Unions: What to Expect in Your 2023 NCUA IT Exam. - OCC Cybersecurity Supervision Work Program (CSW)
The OCC announced in 2018 that they had implemented the FFIEC CAT into their IT examination process. Then, in June 2023, the OCC announced an update to their Cybersecurity Supervision Work Program (CSW). The FFIEC CAT is referenced by the program, alongside other industry frameworks. The CSW stated, "The OCC continues to encourage, but does not require, the use of standardized approaches to assess and improve cybersecurity preparedness."
What This Means: The federal banking agencies' current examination programs continue to reference the FFIEC CAT as a way to assess a financial institution's cybersecurity preparedness. While this could change in the future, as of this publication, the FFIEC CAT continues to be a valuable input into the IT examination process.
4. CAT Approved Through September 2025
If a government agency wants to collect information from the businesses they regulate, they have to get the information collection approved by the Office of Management and Budget (OMB). The OCC (on behalf of the FFIEC member agencies) has been getting the CAT approved by the OMB every year or two since it was first released.
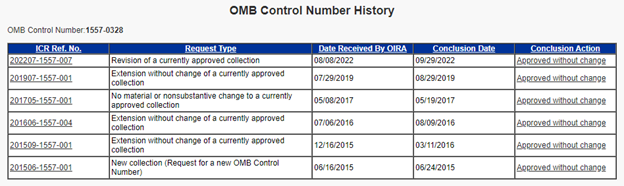
Following the OCC's most recent request for comments published in the Federal Register in August 2022, the CAT was resubmitted for approval. It was approved through September 30, 2025.

What This Means: The FFIEC does not legally have to make any changes to the CAT until the next time they want to get it approved by the OMB in 2025. Of course, they can make updates before then if they want to, but in the government's eyes, the current CAT is good to go for the next two years (or so).
5. Feedback from Industry Groups
When the FFIEC has opened comment periods on the CAT (as is required for approval by the OMB), private industry groups have encouraged the FFIEC to replace the CAT with another industry framework.
For example, the creators of the CRI Profile (a.k.a., "FSSCC Cybersecurity Profile" and "Cyber Risk Institute Profile") have asked the FFIEC on multiple occasions to replace the CAT with their own private industry framework.
Here are links to the public comment letters submitted by these groups, as documented on the Office of Management and Budget (OMB) website:
- Public Comment Letter on 09/22/2015
- Public Comment Letter on 01/15/2016
- Public Comment Letter on 06/06/2019
- Public Comment Letter on 09/07/2022
On behalf of the FFIEC member agencies, the OCC responded to the latest comment:
"As noted above, [a] financial institution's use of the [CAT] is voluntary. While FFIEC members have emphasized the benefits of using a standardized approach to assess and improve cybersecurity preparedness, they have also recognized that institutions may [choose] from a variety of standardized tools aligned with industry standards and best practices to assess their cybersecurity preparedness."
The response adds a footnote to the FFIEC Press Release from August 28, 2019, which reads:
"Institutions may choose from a variety of standardized tools aligned with industry standards and best practices to assess their cybersecurity preparedness. These tools include the FFIEC Cybersecurity Assessment Tool, the National Institute of Standards and Technology Cybersecurity Framework, the Financial Services Sector Coordinating Council Cybersecurity Profile, and the Center for Internet Security Critical Security Controls."
This is most recently restated in OCC Bulletin 2023-22, which says:
"The OCC continues to encourage but does not require use of standardized approaches to assess and improve cybersecurity preparedness, and banks may choose from a variety of tools and frameworks available."
What This Means: The FFIEC is welcoming of many ways to assess cybersecurity preparedness. As long as a financial institution is measuring control maturity in some industry-accepted way, the method is less important than the result.
6. The CAT's Popularity
Based on data from the 2022 Tandem State of Cybersecurity Report, the FFIEC CAT remains the most popular cybersecurity framework, with more than 91% of financial institutions reporting use. Other notable responses include the NIST Cybersecurity Framework (39%) and the Center for Internet Security (CIS) Controls (23%).

What This Means: In spite of the FFIEC acknowledging the use of other assessment frameworks, community financial institutions continue to depend largely on the FFIEC CAT as their cybersecurity assessment of choice.
In Summary: What's Next for the FFIEC CAT?
The CAT is still the industry's assessment of choice. We expect that a tool to help the financial industry measure cybersecurity will continue to be relevant in the months and years to come. Right now, that tool continues to be the CAT.
But we all know it's getting older by the day. A consequence of longevity is that the CAT is beginning to show its age. The frameworks and guidance on which the CAT was built have been (or are actively being) updated, while the CAT itself has not seen an update to its assessment content since 2015.
Some say the CAT needs to be replaced. Certain advocacy groups in the financial industry say the CAT needs to be replaced by another tool, such as the CRI Profile. While the FFIEC continues to respond that financial institutions may use whatever tool they wish, there has been no indication that the FFIEC plans to discard and replace the CAT with a tool created by a private group.
The decision remains with the FFIEC. The FFIEC has not announced any plans for the CAT. If we know anything from watching the FFIEC's previous decisions, they are more likely to make updates to their own assessment (one that has been so thoroughly engrained in the financial sector) than to abandon it. Even with that prediction, no one really knows what will be happening next for the CAT. For now, we wait.
What Does This Mean for You?
While we wait to see how this all shakes out, here are four things you could do to help pass the time.
- Continue to assess your cybersecurity preparedness. While there are lots of options out there, the CAT continues to be the only assessment tool created specifically for the financial industry by federal regulators.
- Don't be afraid to move past "Baseline." If you continue to use the CAT, know that with the emergence of new guidance and regulatory updates, "Baseline" standards from 2015 may no longer be considered "Baseline" in 2023. If you haven't already, start looking at the "Evolving" and "Intermediate" maturity levels.
- Let your voice be heard. If you have questions or comments about the CAT, communicate those with your advocacy groups, talk with your examiners, or look for comment opportunities when they open. The OCC will likely open another comment opportunity in the Federal Register in spring or summer of 2025, if not sooner.
- Check out Tandem Cybersecurity. The Tandem Cybersecurity product is based on the CAT and offers helpful features to improve collaboration and productivity, including notifications, file attachments, presentation reports, peer analysis, and more. At Tandem, it is our goal to ease the burden of regulatory compliance while increasing the security posture of your institution. What this means is that we are waiting for an update to the CAT right alongside you. Let's wait together. Sign up for the free version of our product now at Tandem.App/Cybersecurity-Assessment-Tool-FFIEC.