The Department of Justice recently finalized a new rule on Preventing Access to U.S. Sensitive Personal Data and Government Related Data by Countries of Concern or Covered Persons. This new rule requires anyone who is performing "restricted transactions" to implement a Data Compliance Program by October 6, 2025.
But first, what is a "restricted transaction?"
It's kind of a long answer that needs an entire blog to explain. To really know if you perform "restricted transactions," you should work with legal counsel.
As a rough paraphrase though, a "restricted transaction" happens when you allow a country of concern or covered person access to government-related data or bulk U.S. sensitive personal data via vendor agreement, employment agreement, or investment agreement.
If you perform these restricted transactions, you are legally required to implement a Data Compliance Program, secure those transactions using the (appropriately named) CISA Security Requirements for Restricted Transactions, and have the whole thing audited annually.
Data Compliance Program
Let's take a look at how you can build this Data Compliance Program with Tandem.
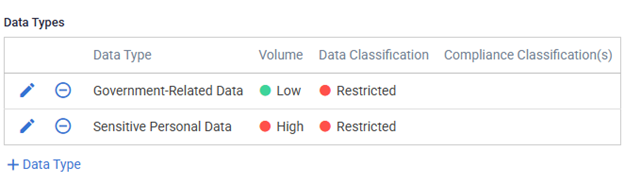
Step 1: Know Your Data
For restricted transactions, you must have procedures in place to identify, verify, and log:
- The types and volumes of covered data involved.
- The involved parties (including ownership, citizenship, or primary residence).
- The end-use of the data.
- The method of data transfer.
Tandem Risk Assessment can help you document an inventory of data types using the Information Assets feature. With this feature, you can associate data types with applicable information assets and vendor services. You may also create and use custom fields to track specific details about each data transaction.
Example
Step 2: Know Your Vendors
If you perform restricted transactions via vendor agreements, you must have procedures in place to verify vendor identities. This is ideally addressed in your vendor management policy and program.
Tandem Vendor Management helps you organize and manage your vendor due diligence records.
- Use the Vendor Profile and Contact Information features to track ownership and identity information about the vendor.
- Label vendors which may be classified as a "covered person" with the Compliance Categories feature to enable quick reporting.
- Store due diligence documents and perform reviews (e.g., SOC report reviews) related to any restricted transactions performed with the vendor.
Learn more in the Tandem Vendor Management Workbook.
Example

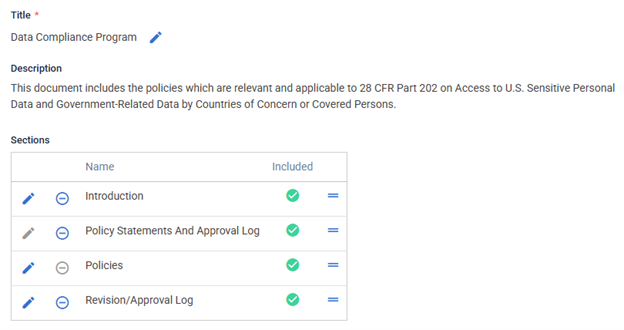
Step 3: Write a Compliance & Security Policy
There's no need to start from scratch when you already have policies which address the compliance and security concepts required in the rule. Don't just take our word for it. This idea is supported by the DOJ in the preamble:
"The Department expects that many companies will adapt their existing compliance programs to respond to the rule's requirements."
To that end, Tandem Policies features several template policies related to this topic.
|
Policy Name |
This policy defines a process for: |
|
Data Management |
Securing data at all phases of the data management lifecycle (i.e., creation, storage, use, retention, and destruction). |
|
Vendor Management |
Securing vendor relationships at all phases of the vendor management lifecycle (i.e., selection, due diligence, contracts, monitoring and reporting, and termination). |
|
Personnel Security |
Securing human resources processes (e.g., hiring, onboarding, ongoing reviews, termination, etc.) |
|
Ethics |
Conducting business with integrity and ensuring financial safety and soundness as it relates to a variety of situations, including investment agreements. |
|
Information Sharing |
Securing voluntary information sharing practices, including data brokerage activities. |
|
Security Testing |
Performing regular assurance and testing activities for security controls. |
Other relevant template policies may include Access Control, Cloud Computing, User Authentication, Artificial Intelligence (AI), Network Monitoring and Log Management, IT Asset Management, and more.
A few additional notes:
- Based on the Questionnaire, applicable policies now include suggested language about implementing and/or auditing the CISA Security Requirements.
- Use the Custom Documents feature to build a dedicated "Data Compliance Program" policy document that packages together the applicable policies.
- Document the required annual policy approval using the Revision/Approval Log.
Example
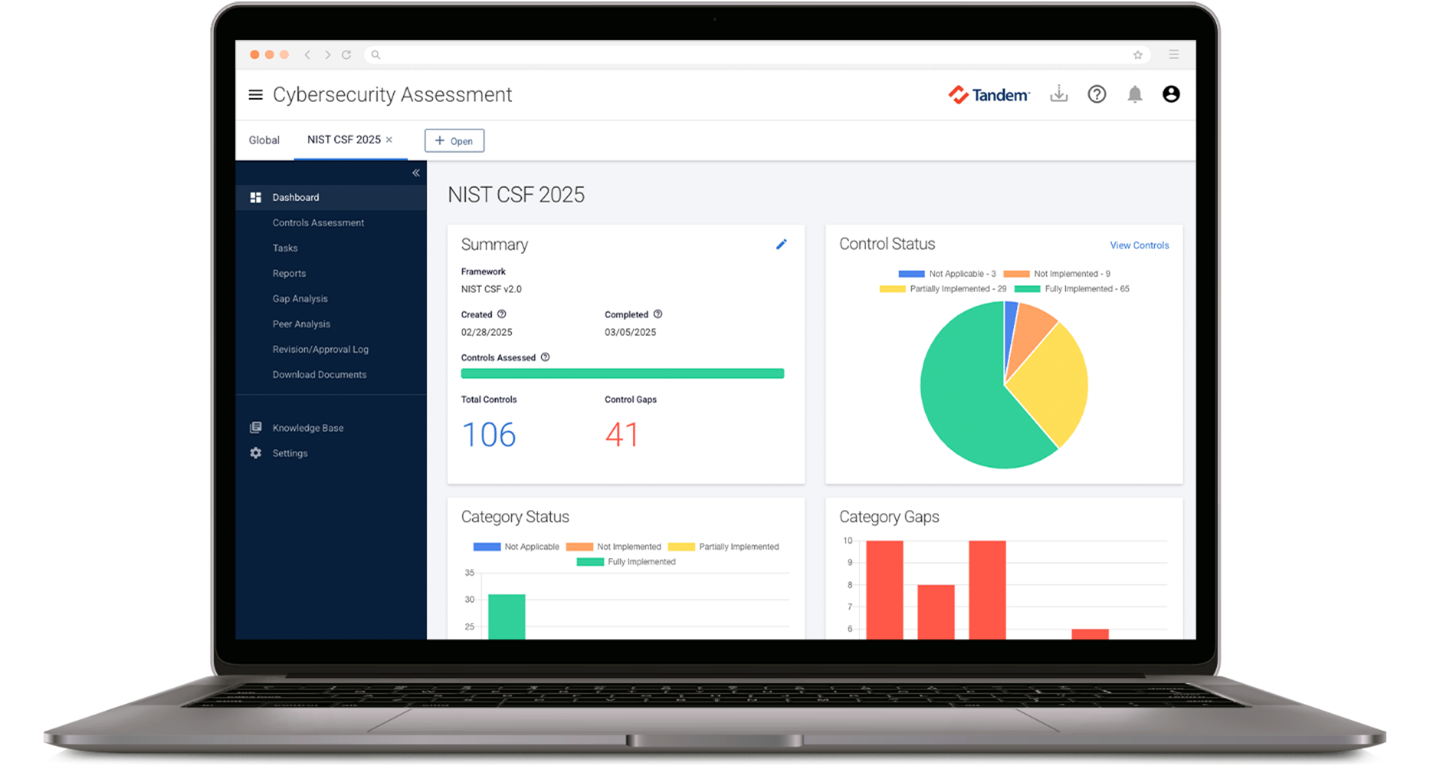
Step 4: Implement the CISA Security Requirements
As mentioned before, restricted transactions are required to be secured in compliance with the CISA Security Requirements for Restricted Transactions.
Tandem Cybersecurity Assessment helps you conduct and document a cybersecurity self-assessment based on the requirements. Sign up for free at Tandem.App/Cybersecurity.
Example

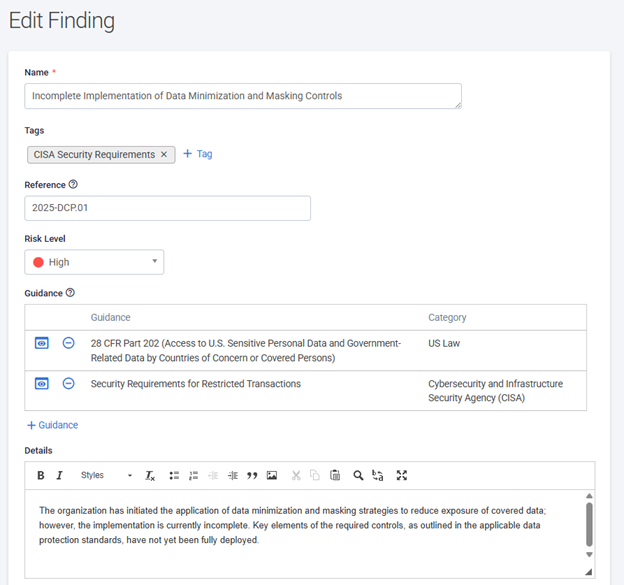
Step 5: Document Audit Findings & Track Remediation Status
You are required to have an annual audit to examine the restricted transactions, the data compliance program, relevant records, and the implementation and effectiveness of the CISA Security Requirements.
Tandem Audit Management is a finding tracking and response software which allows you to document details about your audit, maintain a record of the audit's findings, and track the finding response process. Use the product's helpful features, like notifications, access roles, functional reports, and presentation documents to prove your compliance.
Example
Want to See More?
Tandem is built to improve your cybersecurity governance, risk management, and compliance (GRC) activities. If you'd like to learn more about how Tandem can help you, watch a demo or sign up for free access to Tandem Cybersecurity Assessment.