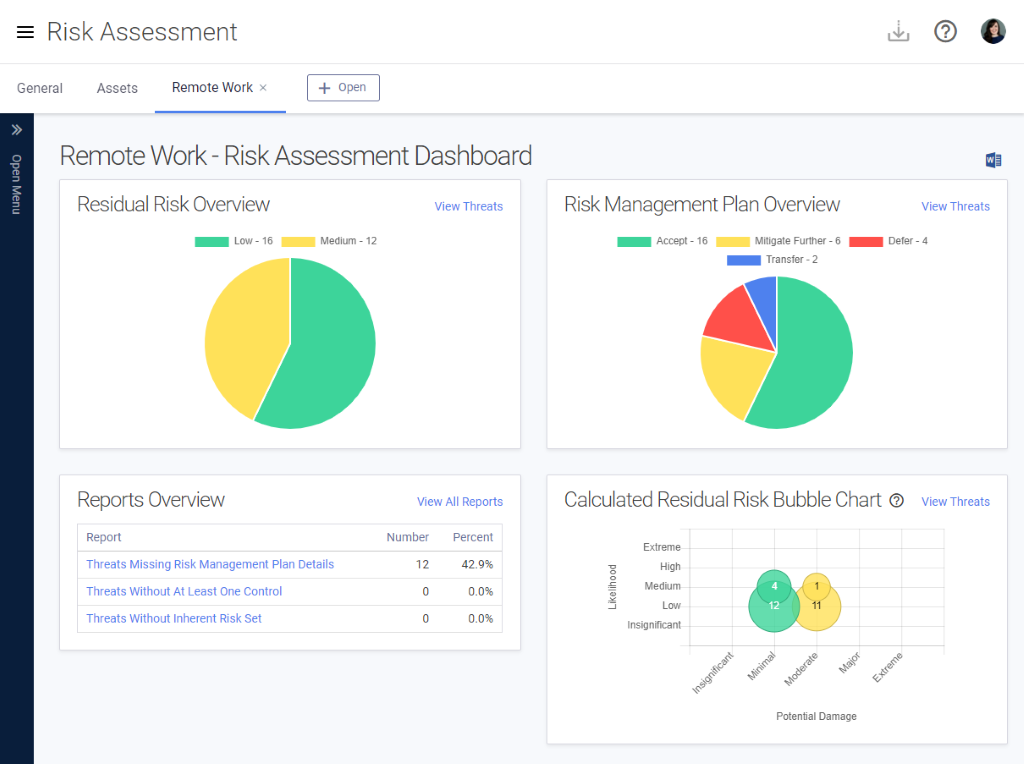
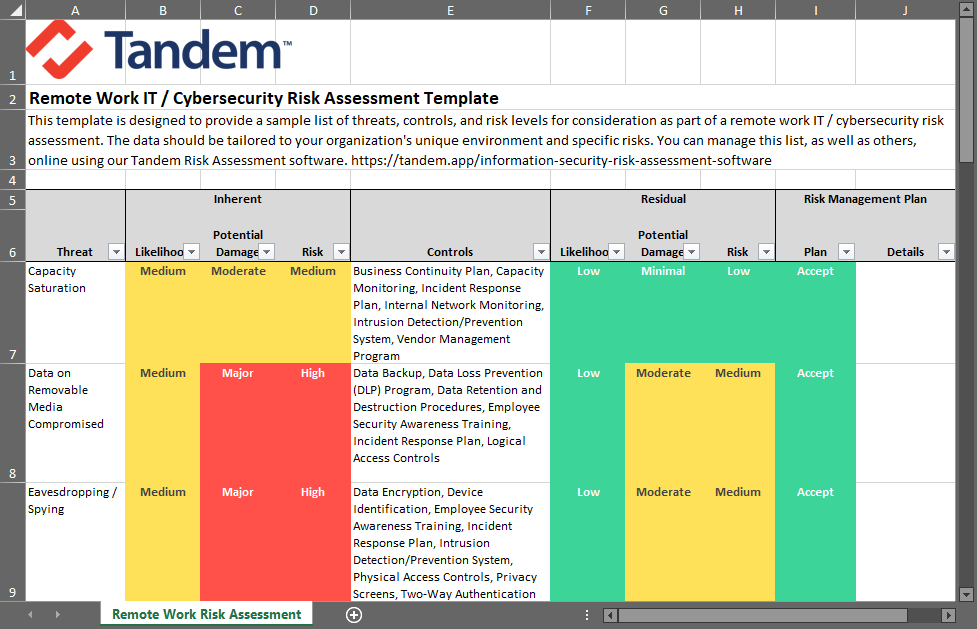
Securing customer, member, and organization data while employees work remotely is a timeless topic, but it takes on a unique angle when organizations are doing so out of an effort to continue operations amid a pandemic.
In our current environment, the difficulty of securing remote staff operations is amplified from multiple angles. A significant percentage of employees are working remotely, employees may have to use unfamiliar systems to get the job done, and bad actors are taking advantage of the unique environment to target remote workers. Each of these factors has led many to ask the question:
How can you ensure employees who work from home are doing so in a secure fashion?
You will find the answers you seek in a remote work risk assessment. Performing this kind of assessment:
- Allows you to identify reasonably foreseeable threats.
- Helps you validate which controls are implemented.
- Enables you to make informed risk management plans.
Identify Reasonably Foreseeable Threats
Identifying reasonably foreseeable threats is a benefit of any information security risk assessment. In the case of a remote work environment, typical information security threats should be reevaluated from the unique form they take in this environment. For example, consider a threat like unauthorized use. While this threat could occur within organization systems and data when an employee is in the office, how much more likely is it that a business system (like a laptop or corporately licensed application) may be used for non-business purposes when staff work from home?
You can best protect your organization's systems and information when you are aware of the risks facing it. For more on this topic, check out our blog on Five Threats to Consider in your Work from Home Risk Assessment.
Evaluate and Implement Controls
Through the application of controls, an organization can reduce the likelihood or potential damage of identified threats. Continuing with the example of a threat like unauthorized use, you may wish to consider implementing controls around enhancing or expanding your employee security awareness training or limiting local administrator access on remote work devices. Both controls, if implemented correctly, could considerably reduce the likelihood and/or potential damage of unauthorized use.
When you are successful in preventing, detecting, or correcting a remote work threat's occurrence or damage, you can better secure your customer, member, and organization data. Learn more about how to secure your data in our article on Key Remote Work Controls to Evaluate and Implement.
Make Risk Management Plans
Once threats have been identified and controls have been applied, what is your organization going to do with the leftover risk? With our example of unauthorized use, even after we implemented additional controls to reduce the likelihood and potential damage of this threat, residual risk remains due to the fact the employee's device is (quite literally) not in your hands.
In a remote work environment, it may be tempting to think ongoing risk management plan options are limited, but several practical options are available. To learn about these options, visit our blog on Developing Accurate Remote Work Risk Management Plans.
Next Steps
If you are ready to get started on your remote work risk assessment, check out one of our other articles linked above or Download our Remote Work Risk Assessment Template. Designed to help you assess the risk of remote work threats, you can use the template to help you ask questions about your remote work environment, identify applicable threats and controls, and document your risk management plans.
Take Your Risk Assessment to the Next Level
To take your remote work risk assessment to the next level, learn more about Tandem Risk Assessment. In addition to the features offered by a spreadsheet, Tandem can help you more efficiently manage your cybersecurity risk assessments with additional templates, access roles, presentation documents, email notifications, and more.