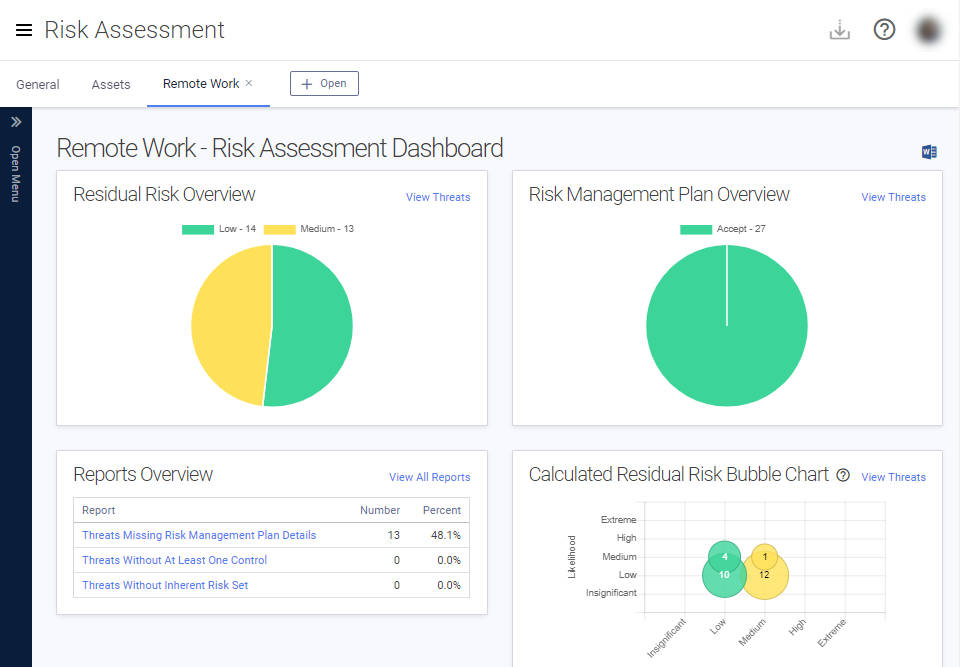
If you have decided to conduct a work from home risk assessment, the first step in the process is to identify reasonably foreseeable threats. In the context of a remote work environment, you should be evaluating people, process, and technology threats. The success of such a threat may result in the compromise of your customer, member, or organization data. Here are five threats to keep in mind, as you begin your risk assessment.
1. Data on Removable Media Compromised
This threat involves information being removed from organization systems on unauthorized removable media (e.g., hard disks, flash drives, smart devices, etc.).
While this threat is applicable regardless of an employee's physical work location, a remote work environment introduces unique factors, such as:
- Easy access to personal removable media devices.
- Temptation to use personal devices for business purposes.
- Unauthorized individuals with access to removable media devices containing sensitive business information.
If not carefully controlled, the occurrence of this threat could result in unauthorized disclosure, misuse, or destruction of valuable information.
2. Exploitation by Cyber Attack
A cyber attack is defined by the Federal Financial Institutions Examination Council (FFIEC) as:
"An attack via cyberspace, targeting an institution for the purpose of disrupting, disabling, destroying, or maliciously controlling a computing environment / infrastructure; destroying the integrity of the data; or stealing controlled information." – FFIEC Information Technology Examination Handbook, Information Security Booklet, Page 77
While exploitation by cyber attack is likely going to be a top threat in any kind of technical assessment, some factors which may increase the risk of this threat when employees work from home include:
- Challenges with patching systems in a timely manner.
- Expanded threat landscape due to employees connecting from numerous untrusted locations.
- Limited protection of home systems due to a lack of knowledge or lack of tools typically available on in-office systems (e.g., anti-malware, firewalls, filters, etc.).
These factors can result in an increased likelihood and potential damage of a cyber attack. Depending on the nature and intensity of a successful cyber attack, an organization could experience unauthorized disclosure, misuse, alteration, or destruction of confidential information.
3. Phishing
Phishing is defined as:
"A digital form of social engineering that uses authentic-looking—but bogus—e-mail to request information from users or direct them to fake websites that request information." – FFIEC Information Technology Examination Handbook, Information Security Booklet, Page 84
Phishing continues to be a persistent threat against employees and can often result in the same outcomes as an exploitation by cyber attack. A few special factors that increase the risk associated with phishing attacks in a work from home environment include:
- Employees working from home may be more relaxed with security practices or reporting protocol, due to the personal and familiar environment.
- The home offers different and potentially increased distractions which do not exist in the office (e.g., family members, pets, access to home amenities, etc.).
- Working from home can increase the commonality of electronic communication, such as email, to share information.
Employees must remain mindful and prepared for the threat of phishing, especially when working from home.
4. Installation of Unauthorized Software
This threat is about software applications being installed on business systems by employees without permission. These applications could be unlicensed, illegal, or even malicious.
In a telework environment, an increased likelihood of this threat may occur for business or personal purposes (e.g., video conferencing, messaging, file sharing, etc.). If not accounted for in the organization's software inventory, vendor management program, and patch management processes:
- Vulnerable applications may exist on organization systems.
- Organization, customer, or member data may be exposed to unauthorized third parties.
While many employees may have good intentions of being able to continue operations in their remote environment, installation of unauthorized software can expose the organization to an increased risk of the unauthorized disclosure, misuse, alteration, or destruction of essential data.
5. Unauthorized Use
Simply put, this threat is about unapproved use of an organization's information assets or data.
When employees work in an office environment, there is a risk of unauthorized use. That said, when employee workstations are taken home, the risk of unauthorized use increases as the system and data is more easily accessible by family members, roommates, pets, etc.
Whether your concern is about a nefarious housemate or a four-legged friend who thinks the keyboard keys look like snacks, it is important to consider and account for the potential unauthorized disclosure, misuse, alteration, or destruction of data or systems due to unauthorized use in a remote work environment.
What's Next?
Identification of threats is the first step in performing your remote work risk assessment, so you can begin to have conversations about how to protect yourself from such an event. Learn more about how to protect your organization from these and other threats in our article on Key Remote Work Controls to Implement and Verify.
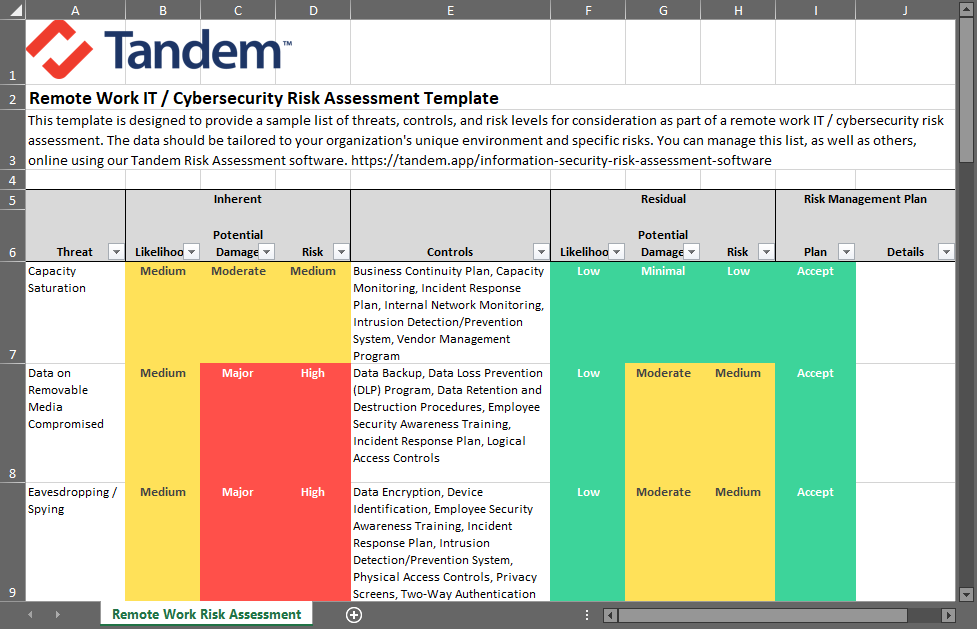
If you are ready to start your remote work risk assessment, Download our Remote Work Risk Assessment Template. Designed to help you assess the risk of remote work threats, you can use the template to help you ask questions about your remote work environment, identify applicable threats and controls, and document your risk management plans.
Take Your Risk Assessment to the Next Level
To take your remote work risk assessment to the next level, learn more about Tandem Risk Assessment. In addition to the features offered by a spreadsheet, Tandem can help you more efficiently manage your cybersecurity risk assessments with additional templates, access roles, presentation documents, email notifications, and more.