In the process of conducting a work from home risk assessment, once you have identified reasonably foreseeable threats to your organization and data, the next step is to evaluate and implement controls.
As you consider controls, there are two categories to keep in mind:
- Timing of controls can be preventative, detective, or corrective. In other words, controls which could reduce the likelihood or damage of a threat before, during, and after the threat occurs.
- Nature of controls can be administrative, technical, or physical. Examples of administrative controls include policies, technical controls include scans or filters, and physical controls include tangible barriers.
In order to have a strong layered security program, you should ideally implement a control from each timing subcategory for each threat. You should also be able to recognize the benefits and limitations associated with certain types of nature controls. For example, it may be challenging or even impossible to implement physical controls in your employees' remote work environments. As such, you should consider additional administrative or technical controls to compensate.
While each remote work function has unique elements, here are some key controls to consider for your remote work environment.
Employee Security Awareness Training
Training employees on security awareness can greatly reduce the risk of threats in a remote work environment. Training is an administrative (nature) control, but is one of few controls which can be preventative, detective, and corrective (all three of the timing subtypes), if implemented correctly.
To determine if this control is implemented appropriately, consider doing the following:
- Review your existing security awareness training policy and course material.
- Verify the training addresses topics related to working from home (e.g., anti-malware, physical security, password complexity, mobile devices, wi-fi security, reporting security issues, etc.).
- Examine results of recent training and determine if outcomes were satisfactory.
- Conduct a standalone assessment (e.g., survey, quiz, simulated phishing campaign, etc.) to see how much employees really know and determine which employees could benefit from some retraining.
To further reduce risk, consider increasing the amount of security awareness training each employee receives. The 2020 State of Cybersecurity survey shows just a couple more hours of security awareness training each year can greatly improve the effectiveness of training and, subsequently, reduce risk.
Employee security awareness training is not an infallible control, but it is foundational in a remote work environment, when so much of the technology is out of the organization's control.
Data Backup
Backing up data on remote work systems is a corrective technical control. If a threat occurs and renders data unusable, an effective data backup control is going to be a valuable tool in resuming operations in a timely manner.
To determine if this control is implemented appropriately, consider doing the following:
- Review your data backup policy.
- Determine if and how data on remote work systems is backed up.
- Verify backup restoration tests have been successfully completed.
Backup data is of no use if it cannot be successfully restored. Periodic testing (e.g., monthly or quarterly) can help ensure this is a feasible control on which your organization can depend.
Data Encryption
Data encryption is an advantageous control to implement for remote work systems. Options include using a virtual private network (VPN) to encrypt data in transit, as well as using a tool (e.g., Bitlocker) to encrypt data at rest. This technical control can be both preventative and corrective, as it not only prevents the success of virtual eavesdropping, but can also protect data in the event a remote work system is lost or stolen.
To determine if this control is implemented appropriately, consider doing the following:
- Review your data encryption policy.
- Evaluate remote work device configuration settings to determine if an encryption tool is implemented for data-at-rest.
- Determine if the organization requires use of a VPN for data transmission to-and-from the corporate network.
- Conduct a vulnerability scan to determine if data is being encrypted successfully.
As employee home offices and networks may not be as secure as those offered by the organization, encryption is one way to help ensure data remains secure.
Limit Local Administrator Access
Restricting remote users' ability to run as a local administrator on their workstations is another technical method of preventing and correcting the risk of certain threats.
To determine if this control is implemented appropriately, consider doing the following:
- Review your user access control policy.
- Evaluate remote work device configuration settings to determine if employees are authorized to run as local administrators on remote work systems.
- Conduct a vulnerability scan to determine if any users have unauthorized elevated privileges.
Limiting local administrator access comes with some costs, such as remote employees being limited in performance of certain functions. However, limiting local administrator access also comes with benefits, such as inability to install unauthorized software or limited damage to the system in the event of the employee falling victim to a phishing or cyber attack.
Patch Management
Having an established patch management process for remote work systems is a preventative and corrective technical control. While many patch management methods exist, at a minimum the organization should have a plan for regular implementation of necessary operating system, firmware, and software application patches.
To determine if this control is implemented appropriately, consider doing the following:
- Review your patch management policy.
- Determine if expectations are outlined for remote systems connecting to the organization network, such as baseline patches which must be installed or existence of an anti-malware solution.
- Review how systems are updated (e.g., automatic updates, push updates when connected via VPN, manual inspection and update, etc.), so you maintain appropriate expectations.
- Conduct a vulnerability scan to determine if required security patches on remote work systems are up to date.
Your network is only as strong as your weakest unpatched system, so a strong patch management program for remote work systems is worth revisiting as employees continue work from home.
What's Next?
Evaluation and implementation of controls is an important step in conducting a remote work risk assessment and ultimately, protecting your customer, member, and organization data. Once controls have been implemented, the next step is to Develop an Accurate Remote Work Risk Management Plan for any residual risk.
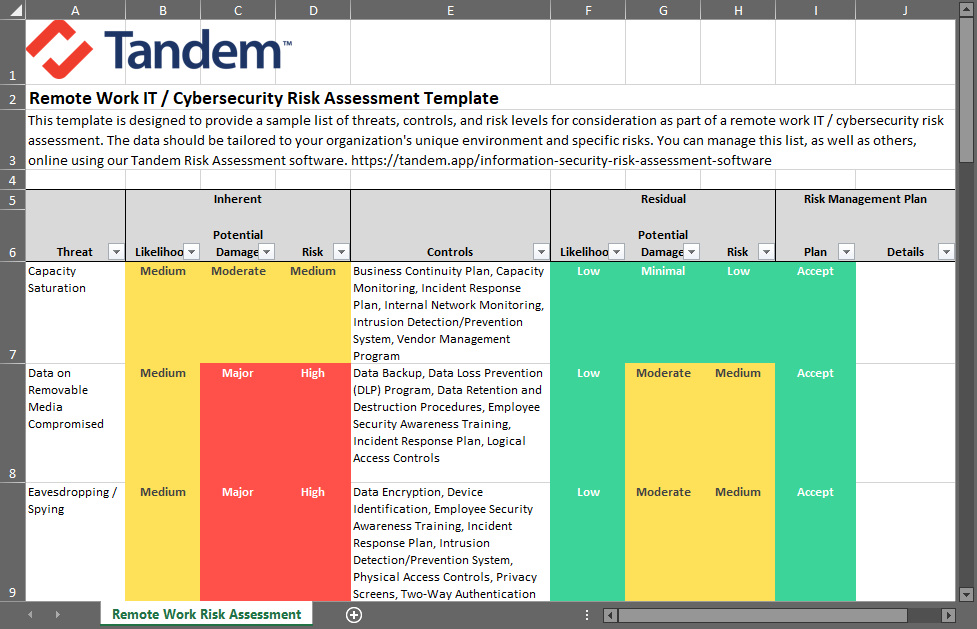
If you are ready to start your remote work risk assessment, download our Remote Work Risk Assessment Template. Designed to help you assess the risk of remote work threats, you can use the template to help you ask questions about your remote work environment, identify applicable threats and controls, and document your risk management plans.
Take Your Controls to the Next Level
To take your controls to the next level, learn about Tandem Policies. Maintain a living set of information security policies that is easily accessible with Tandem's flexible policy framework. Tandem offers customizable language for more than 50 template policies, designed to address topics such as employee security awareness training, data backup, data encryption, user access control, and patch management.