If you asked a hundred Information Security Officers (ISOs) about their favorite part of the job, I would be willing to venture a guess that exactly zero of them would respond with anything related to the organization's information security policies. This is a tragedy, my friends.
Just like you and me, information security policies have a purpose. They have a rich history, and they exist for a reason besides taking up your valuable time. In this article, I'm going to show you why your policies are important and give you six tips to make sure they live up to their fullest potential.
Why Information Security Policies?
There are three primary reasons why you should have effective information security policies. Repeat after me: G-R-C (governance, risk, and compliance).
- Governance. NIST tells us that policies are a series of "statements, rules, and assertions that specify the correct or expected behavior of an entity." In other words, information security policies tell you what to do and what not to do to make the business run effectively and safely. They do this by defining things like expected behavior, required actions, and prohibited activities. In other words, they govern.
- Risk. Since policies define how the business is expected to run, policies also define the institution's control environment. Specifically, information security policies provide a framework for mitigating the risks identified in the organization's GLBA risk assessment.
- Compliance. Of course, financial institutions are also expected to have information security policies. This requirement stems from the Gramm-Leach-Bliley Act (GLBA), the resulting Interagency Guidelines Establishing Information Security Standards, and the FFIEC's Information Security Booklet, Section II.C.1 Policies, Standards, and Procedures.
Effective information security policies are key to helping your business thrive. When managed with care, policies can be relied on not only as an item on the compliance checklist, but also as a decision-making tool and a means of protecting your organization.
Check out our eBook to see how policies fit in to your overall information security program.
6 Tips for Writing an Effective Information Security Policy
The best information security policies are the ones everyone can understand and follow. To that end, there is no one right way to write an information security policy. However, in the 15+ years of Tandem's experience writing information security policies, we've learned a thing or two we think might be helpful.
Tip #1: Create One Policy from Many Policies
One question we receive regularly is, "Should I have one information security policy or many information security policies?"
Our answer is "yes." We believe the best information security policy (singular) is made up of many information security policies (plural). For example, some of your information security policies exist to define administrative practices (e.g., acceptable use), while others discuss technical safeguards (e.g., encryption), and others still, your physical controls (e.g., facilities security).
Instead of writing one lengthy policy which is extremely broad and nearly impossible to manage, much less read, we find it is much more effective to manage several smaller individual policies which roll-up under the singular umbrella policy document.
Tip #2: Represent all Stakeholders
It is a common belief that policies are a "top-down" communication tool, which makes sense. Policies are written to communicate the Board's expectations for the rest of the business, which is why the Board needs to approve them at least annually, per GLBA. The Board is ultimately responsible for the successes and failures of the policies.
That said, who actually writes the policies? Well, if you're reading this article, it's probably your non-Board-member-self, right? You write the policies because you are closest to your team members and the day-to-day operations of the business. You represent every employee when you write policies to present to the Board. So, while policies are indeed "top-down," they are also "bottom-up."
When you write a policy, it is so important to frame it in this mindset to make sure the policy clearly communicates what it needs to say on behalf of all stakeholders. This means representing not only the Board who sets the direction, but also the people who will be putting the policy into action.
Tip #3: Break the Text Up
You've heard of picky eaters? Well, my name is Alyssa, and I am a picky reader. Don't get me wrong, I love reading, but living in the era of "there's probably a summary of this on YouTube," I've become very selective with how I spend my time reading.
If I open a document and I just see a wall of text, I'm probably going to look for the CliffNotes. On the other hand, if I open a document and find something that is visually interesting with headings and keywords… Let's be honest, I may still go find the CliffNotes, but it will keep my attention longer.
Let me give you an example. Which of the following pages would you be more likely to read and comprehend?
|
Page A
|
Page B
|
I rest my case.
(Fun fact, both images are from the FFIEC Retail Payment Systems booklet. Page A contains text written in 2004. Page B contains text written in 2016. Most of the booklets published since 2016 look more like Page B, so major kudos to the FFIEC for trying to make guidance more readable!)
We know people's attention spans are short and walls of text are difficult to process. This is part of the reason why we break each of Tandem's information security policies into multiple sections. Some sections you'll find in our policies include the Policy Statement, Commentary, Implementation, Related Policies, Responsibility, Review Items, and more.
By splitting a policy into several sections, you can make it easier for your readers, which ultimately benefits both you and them. When a policy is readable, this makes it more likely to be read, and easier to update and maintain over time.
Tip #4: Look to the Experts
I don't know about you, but for me, one of the most difficult parts of any writing project is putting the first paragraph on the page. What do I want to say? What tone should I approach this with? How can I make this most valuable to the reader? Why am I here? It is very difficult to start from scratch, so my best advice to you when it comes to writing a policy:
Don't start from scratch.
There are some excellent guidance documents, standards, and frameworks already out there which are designed to give you an idea of the things you need to do to protect your organization. As a result, they would be great topics to consider using as the foundation of your policies. Here is my default "go-to" list:
- FFIEC IT Examination Handbook
- FFIEC Cybersecurity Assessment Tool
- NIST Cybersecurity Framework
- NIST SP800-53 Controls
- CIS Controls
- CISA Tips
- CISA Alerts
- Agency IT Examination Procedures (e.g., FDIC InTREx Program)
- Agency Guidance
When it comes to writing information security policies, these are a million and one agencies providing recommendations about how to secure your organization. The trick is knowing how to find it.
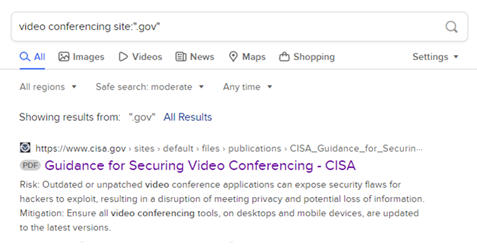
If you're having a hard time knowing where to begin, pull out your favorite search engine and type this magical string of characters:
[Topic] site:".gov"
For example, if you were going to write a policy about securing video conferencing tools, you could type:
Video Conferencing site:".gov"
What this tells the search engine is that you want to see any and all resources on the topic of video conferencing from government websites. Wouldn't you know it? You'll often find exactly what you hoped to see. (And if you don't, you can always refine your search terms a bit.)
Tip #5: Invest in a Policy Management Product
So, we've already established you don't have to start from scratch. Let's take this step further: Start from an existing policy. Policy management products are designed to help make maintaining policies easy. As part of that, many of these products include templates which are designed to help jump-start your policy writing process.
Of course, these policies are not intended to be used straight out of the box because they may not accurately reflect your business or your stakeholders. But if you can find a policy management product, like Tandem Policies, it can boost your writing process and make drafting policies a whole lot more manageable.
Tip #6: Be Clear
One of my favorite quotes from Brené Brown is this: "Clear is kind. Unclear is unkind."
While this applies to all forms of communication, I think it is especially important in the world of policy writing. We write policies to communicate with people. If communication isn't happening, we need to take a step back, figure out why, and work it out.
If I could make one recommendation here, it's this: Be direct with your words.
Policies don't need to be complex. They don't need to be written in legalese. Above all, they must never contain the word "should." "Should" leaves too much wiggle room. For example:
- Instead of saying: "You should lock your computer screens anytime you leave your desk for an extended period of time."
- Try saying: "Lock computer screens when they are not in use."
The same message is communicated, but the word count is more than halved and the sentence communicates a direct expectation instead of a wishy-washy recommendation.
In Summary
Policies are meant to be living documents. They exist to provide structure for your operations, guide your decision-making processes, and mitigate the risks facing your organization. If your information security policies don't quite measure up, it might be time to revisit your policies and see what you can do to level up.
If you are ready to take the next step, check out Tandem Policies. Our policy management software comes populated with a list of more than 50 information security policy templates, designed to give you the boost you need to help you maintain a living set of policies. Some examples of our recommended policies include Change Management, Data Backup, Incident Management, Personnel Security, Vendor Management, and more. Learn more at Tandem.App/Policies-Management-Software.