On March 1, 2023, the Federal Home Loan Mortgage Corporation ("Freddie Mac") published Bulletin 2023-6. The bulletin announced an update to Freddie Mac's information security and privacy requirements. Here's an introduction to the requirements, as well as a summary of what's new, what's changed, and what you may need to do about it.
Note: The requirements discussed in this blog only apply to single-family seller servicers. To see the existing multifamily seller servicer information security requirements, see Section 2.26 "Information Security" of the Multifamily Seller Servicer Guide.
About the Requirements
Freddie Mac's information security requirements can be found in Section 1302 of The Single-Family Seller Servicer Guide (a.k.a., "the guide"). Any organization that acts as a seller or servicer of loans sold to Freddie Mac is expected to comply with the guide, as it is part of the "Purchase Documents."
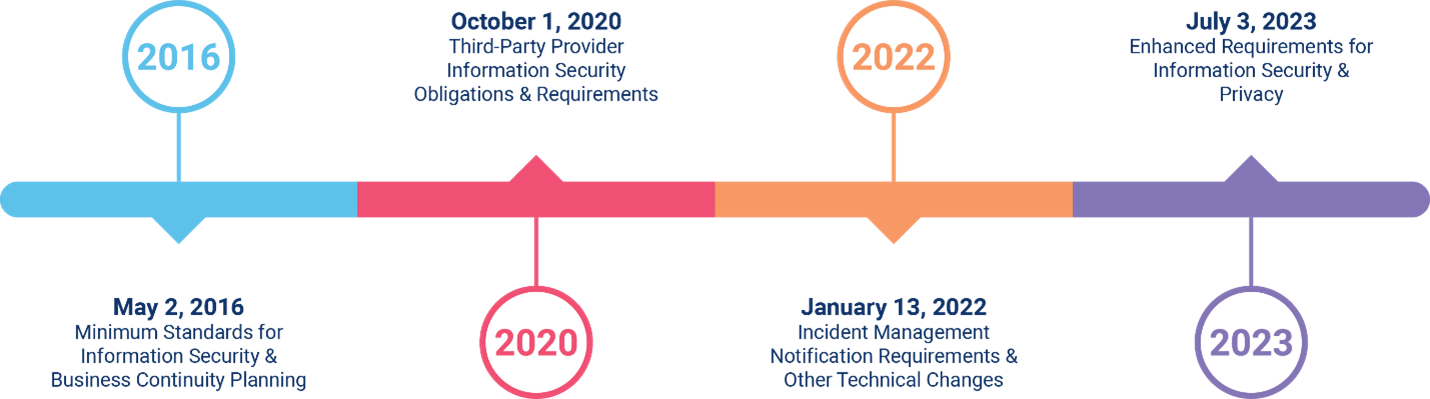
Here is a brief history of The Guide's information security requirements.
- May 2, 2016
This was the effective date for the first "minimum standards" in the guide for information security and business continuity planning. The guide included baseline recommendations for maintaining information security policies and procedures, as well as implementing physical, technical, and administrative controls. For more details, see Bulletin 2015-19 (page 13). - October 1, 2020
A modification was made to the requirements to clarify that the requirements extended to third-party providers. Each business needed to not only maintain their own information security program, but they needed to expect their third parties to also "safeguard and maintain the security, confidentiality, and availability of systems, data, and information." For more details, see Bulletin 2020-18. - January 13, 2022
Modifications were made to the requirements, including an update to require notice to Freddie Mac within 48 hours of a security incident. For more details, see Bulletin 2021-31. - July 3, 2023
The new and revised information security requirements will go into effect on this date. For more details, see Bulletin 2023-6.
In short, Freddie Mac's information security requirements have existed and been refined several times over the years. What's notable now is that these requirements include the biggest changes since the original publication. So, let's spend some time diving into those updates.
What's New
The revised information security requirements include several wholly new provisions which were not previously addressed in the guide. Here's a listing of the new requirements.
|
Section ID |
This section requires organizations to: |
|
1302.2(b)(viii) |
Have a written mobile device management (MDM) policy that addresses security best practices, like approved and prohibited apps, encryption, access controls, and patching best practices. |
|
1302.2(b)(xii) |
Implement logging and monitoring best practices, as well as an independent security assessment (i.e., "audit") at least annually and in the event of a security incident. |
|
1302.2(b)(xiii)[JE3] [AP4] |
Implement a SDLC process and policy that focuses on security best practices, like separating the production and test environments, secure coding, open-source requirements, and code deployment. This section only applies if the organization develops software internally. |
|
1302.2(b)(xv) |
Develop, implement, and annually test an incident response plan. |
|
1302.2(b)(xvii)(E) |
Have a formal cloud computing policy, if the organization uses cloud services for: · Supporting Freddie Mac systems · Freddie Mac confidential information · Protected information |
While these requirements may be entirely new for some organizations, the good news is that for many banks and credit unions, these practices are already recommended by the FFIEC and federal banking agencies. For more information about how these concepts may already be part of your information security program, download the Freddie Mac Information Security Requirements Workbook.
What's Changed
In addition to the brand-new items, there were a significant number of changes to the information security requirements. While we're going to hit some of the trends in this article, you can see a more comprehensive listing of the changes in Freddie Mac's Information Security and Privacy Updates Fact Sheet.
(In the following tables, items marked with an asterisk (*) are part of the new sections mentioned above. The other items are updates to existing requirements.)
Annual Review & Validation Requirements
Several new annual review and validation requirements appeared in the updates, including the following.
|
Section ID |
This section requires organizations to at least annually: |
|
1302.2(b)(i) |
Review the information security program. |
|
1302.2(b)(iii) |
Perform a physical facility access privilege review. |
|
1302.2(b)(vii) |
Formally recertify and authorize the organization's firewall rules. |
|
1302.2(b)(ix) |
Review wireless networks to verify authorized users and access points. |
|
1302.2(b)(x) |
Have an independent third-party penetration test. |
|
1302.2(b)(x) |
Conduct a vulnerability assessment. |
|
1302.2(b)(xii) |
Have an independent security assessment. |
|
1302.2(b)(xv) |
Test the incident response plan.* |
|
1302.2(b)(xvii)(B) |
Review all user access privileges and certify access. |
|
1302.2(b)(xvii)(D) |
Reconcile the asset inventory management system to the actual inventory. |
What this means is that it is not enough to just have and implement an information security program. Regular review and independent validation are key components in ensuring compliance with the requirements and promoting security.
As an aside, in the banking industry, while it is considered to be a security best practice to perform these items at least annually (and sometimes, more often), it is interesting to note that Freddie Mac included the explicit brightlines (i.e., annual threshold) for these items.
- The argument for brightlines is they can reduce confusion and improve clarity. If you know something must be performed annually, then it must be performed annually. This makes it a good step for organizations which are going from potentially not doing these things at all to at least doing them on a regular basis because they know it's required.
- The argument against brightlines is that in the long-term, they can contribute to a culture (or mindset) of compliance over security. If you know something must be performed annually, then it will be performed annually, even if the organization could do a risk-based analysis that shows it needs to be done more (or less) often.
While the FFIEC agencies have decided to "limit the use of numerical thresholds or other 'brightlines' in describing expectations in supervisory guidance," it is interesting to see how other organizations, like Freddie Mac, continue to use them to promote security goals.
Policies
Several updates were made to require seller/servicers to have specific policies.
|
Section ID |
The organization is required to have a policy that addresses: |
|
1302.2(b)(v) |
Data loss prevention (DLP) |
|
1302.2(b)(viii) |
Mobile device management (MDM)* |
|
1302.2(b)(x) |
Vulnerability assessment |
|
1302.2(b)(xi) |
Patch management |
|
1302.2(b)(xiii) |
Software and application development lifecycle (SDLC)* |
|
1302.2(b)(xiv) |
Encryption and cryptography |
|
1302.2(b)(xvii)(E) |
Cloud computing* |
Policies are a series of statements, rules, and assertions which define the organization's structure. Learn more about what it looks like to write an information security policy in our blog: 6 Tips for Writing an Effective Information Security Policy.
(Better yet, check out Tandem Policies. Our product comes with template policies that address the items listed in Freddie Mac's new requirements. Sign up to watch a demo of how Tandem Policies can save you time and simplify your policy management.)
Third Parties
Three updates were made regarding the legal side of third-party relationships.
|
Section ID |
The organization is required to: |
|
1302.2(b)(ii) |
Have third parties sign an NDA (or code of conduct) on the topic of use, disclosure, and confidentiality of Freddie Mac systems, Freddie Mac confidential information, and Protected information. |
|
1302.2(b)(xvii)(F) |
Have a written agreement with third parties that outlines the minimum requirements associated with storing, processing, accessing, or transmitting Freddie Mac confidential information and Protected Information. |
|
1302.3 |
Designate Freddie Mac as an express, intended third-party beneficiary, except for when the third party already has a direct relationship with Freddie Mac (e.g., mortgage insurance companies, credit bureaus, warehouse lenders, etc.). |
While the first two items on the list may be additional things which need to be done, the third item reduces the regulatory burden, which is always nice to see.
Termination Considerations
Three updates were made to define information security requirements following Freddie Mac's termination of the seller/servicer's right to sell or service mortgages.
|
Section ID |
Upon termination of rights, this section requires the organization to: |
|
1302.1 |
Protect the confidentiality, integrity, and availability of Freddie Mac confidential information and Protected Information retained by the organization. |
|
1302.2(b)(i) |
Provide attestation of the adequacy of information security policies and procedures. |
|
1302.3 |
Be able to maintain and restore retained information, unless permitted to destroy the information. |
Two other considerations related to termination were also included.
|
Section ID |
The organization is required to: |
|
1302.1 |
Comply with all of the requirements. Failure to comply may result in termination of rights to "any or all Freddie Mac systems." |
|
1302.2(b)(xvii)(A) |
Notify Freddie Mac within 24 hours of termination (or transfer) of an employee with user account access to Freddie Mac systems. |
What these updates tell us is that Freddie Mac is taking the security of information seriously, both now and in the future when an organization (or person) no longer does business with Freddie Mac.
How You Can Prepare
Here are four steps you can follow to prepare for the upcoming changes.
- Determine if these changes apply to you. If your business is a single-family seller/servicer of Freddie Mac mortgages, these changes would apply to your organization.
- Compare your current program with the updated guide. Your information security program may already address many of the considerations now required, especially if you work for a business regulated by one of the federal banking agencies (e.g., FDIC, FRB, NCUA, OCC, etc.). If you need help knowing where to look, download the Freddie Mac Information Security Requirements Workbook.
- Watch the webinar recording. On Thursday, May 4, 2023, we hosted a webinar on "Maintaining Compliance with Freddie Mac's New Information Security Requirements." Learn more and sign up to watch the session on-demand at: https://go.tandem.app/mba-webinar/.
- See how Tandem can help. Tandem is designed specifically for financial institutions (e.g., mortgage companies, savings associations, banks, credit unions, etc.). It is our goal to help you improve your information security, stay in compliance, and lower overhead costs. If you're looking for a place to get started complying with these new requirements, we'd recommend checking out Tandem Policies, Tandem Incident Management, and Tandem Business Continuity Plan.
We believe you have what it takes to manage information security and regulatory compliance. With the right tool, you can do it fast. Learn more at Tandem.App.