When a security incident occurs, an early step in the analysis stage is to answer the question, "How bad is it?" Having an intentional approach to answering this question will help you facilitate decision making, prioritize responses, and ultimately, improve your organization's security. In this article, we will review the steps you can take to ensure incidents are classified effectively.
What is Incident Classification?
Incident classification is the process of determining and documenting an incident's categories and severity according to a set of predefined standards.
Benefits of Incident Classification
With an effective incident classification strategy, you can:
- Reduce impulsive decision making. With shared definitions, incident handlers can spend less time trying to label the incident and more time focusing on their role in responding to the event.
- Prioritize incidents. By understanding an incident's severity in relation to other incidents, handlers can focus on priority incidents before responding to lower impact events.
- Quickly initiate response. Classifications can be used to determine specific response steps to be followed and particular people to be notified.
- Improve your response plan. A standard set of classifications makes post-incident activities more effective. The easier you can identify areas of weakness, the sooner you can strengthen your plan.
In summary, classification strategies have a direct influence on the accuracy, efficiency, and effectiveness of your incident response processes.
How to Classify Security Incidents
Step 1: Create your classification strategy.
Choose the types of classifications that will be useful in reaching your incident response goals. We recommend Categories to make it easy to spot trends and Severity to address incidents with the highest impact first. We will be using Categories and Severity in our examples throughout this article.
For your classifications to be most effective, you should have a shared set of definitions. For example, if you have a "Third Party" incident which is "High" severity, your incident response plan should define what each of those terms means.
Category Examples
Some common top-level categories you could add to your plan include:
- Data Breach: Data accessed, modified, and/or exfiltrated by an unauthorized entity.
- Malicious Code: Software applications designed to access a system without authorization, including a variety of forms of hostile, intrusive, or annoying code (e.g., viruses, worms, trojan horses, spyware, ransomware, crimeware, rootkits, etc.).
- Social Engineering: An attack that exploits human nature and behavior to convince the target to perform an unauthorized operation or reveal proprietary information.
- Third Party: An incident originating from or through a third party, causing direct or indirect damage to the organization.
There may be times you wish to classify incidents on a more granular level. For example, instead of just categorizing an incident as "Malicious Code," you may also want to specify the type of malicious code, like "Ransomware." Your list of categories can become lengthy, so as you are defining your categories, keep the purposes of classification in mind. Refer to the above list as a starting point.
Applying categories to an incident can also be used to determine action plans. For example, if an incident was classified as a "Third Party" incident, incident handlers would know to enact the Third-Party Incident Response Playbook. Using categories to determine which response plans should be implemented can help reduce confusion and provide a clear path forward for responding to the incident.
For a full list of categories and definitions, download our Incident Tracking Form.
Severity Examples
A common severity scale we like to use is Insignificant, Low, Medium, High, and Extreme. Consider different kinds of impact to help you define each level. It may be helpful to create a matrix with scaling values to help you determine an incident's severity. Consider the following example:
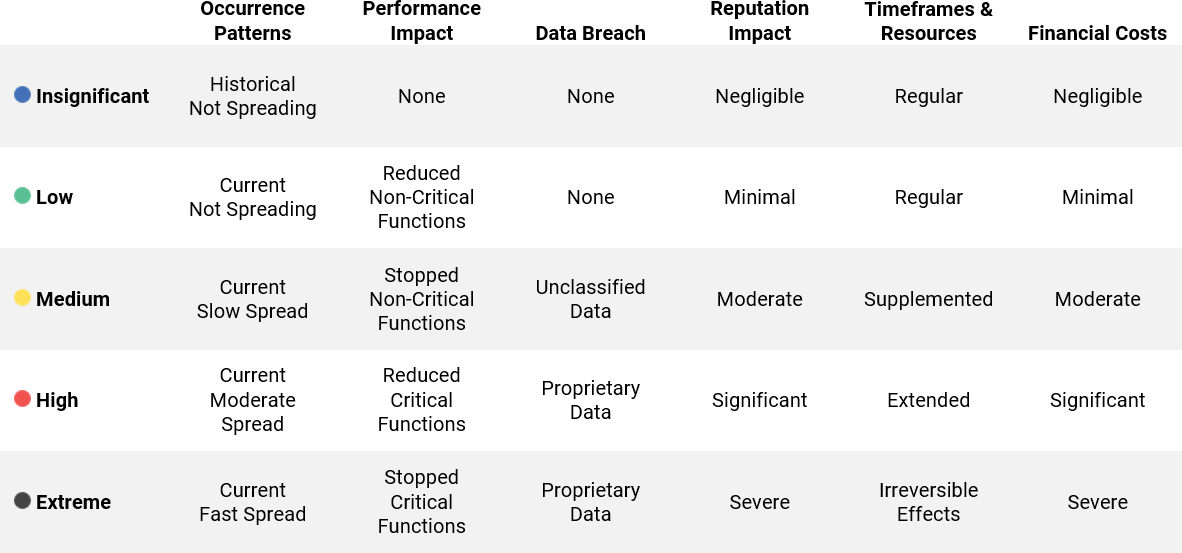
A good severity classification can improve communication and decision making among incident handlers. For a full list of severity level definitions, download our Incident Tracking Form.
Step 2: Apply the classifications to incidents.
When an incident occurs, initial responders can refer to your category and severity definitions to classify the incident. This information can help communicate the nature of the incident, as well as guide escalation procedures. As additional information is learned about the incident through the response processes, incident handlers can update the selected classifications to reflect the impact more accurately.
For example, if an employee reported they received a phishing email to your IT department, this could be initially classified as a "Low Social Engineering" incident. If, however, it was discovered that many employees received the email, and it introduced a malware variant into your systems, that could then become a "High Social Engineering and Malicious Code" incident.
Step 3: Improve the classifications.
During the post-incident activities, review your classifications and update the plan, as needed. Consider the following questions:
- Were we able to clearly determine the categories and severity of the incident?
- If not, what changes would help us do that better in the future?
Use the information learned from these questions to update your incident response plan and improve future incident management processes.
Step 4: Learn from classified incidents.
One of the primary benefits of classification is the ability to generate post-incident comparative reports. These types of reports can help identify root causes and improve your risk management practices.
For example, if you know you've had a 20% increase in the number of successful "Phishing" attacks this year, you may wish to reassess the controls which should be mitigating your social engineering risk (e.g., email filters, security awareness training, anti-malware applications, etc.). By using comparative reporting based on your classifications, you can learn and further improve your organization's security.
What's Next?
If you're looking for a tool to make classifying incidents easier, check out Tandem Incident Management. Designed with incident handlers in mind, Tandem can help you develop your incident response plan and classify incidents in our tracking component. Learn more about Tandem Incident Management at Tandem.App/Incident-Management-Software.


