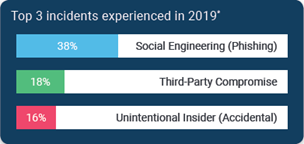
According to the Tandem State of Cybersecurity 2020 Survey Report, the top three incidents experienced in 2019 by financial institutions were social engineering (phishing), third-party compromise, and accidental security incidents by employees.
With lessons learned from Tandem's experience in the security industry and recommendations based on the NIST Special Publication 800-61 Rev. 2, Computer Security Incident Handling Guide, here are seven best practices to help you build your incident response plan and prepare for security incidents.
For a webinar version of this information, watch our recording over How to Create an Effective Incident Management Plan.
1. Define roles and responsibilities
When an incident occurs, stress can be high, and efficiency is vital. While the incident response team will manage the response, it is important to document specific roles and responsibilities, so each team member's purpose is defined, and expectations are clearly communicated. At a minimum, your company should add these roles and responsibilities to your incident response plan:
- Incident Lead: The lead incident handler is the primary contact for responding to a specific incident and manages coordinating activities, gathering information, and serving as a resource for others who are working on the incident.
- Technical Specialist: The technical specialist provides expertise in high-tech areas such as system administration, network administration, intrusion detection, and forensics.
- Legal Advisor: As an incident may involve legal, contractual, or compliance elements, it is important to have legal representation to provide guidance during the response process.
- Public Relations Coordinator: The public relations coordinator oversees communications, developing communication plans and statements, as needed.
Agreed upon incident management roles and responsibilities provide clarity and direction, ensuring successful incident response across the organization.
2. Create classification strategies
Implementing an incident classification system offers diverse benefits. In addition to improved communication, classification can make it fast and easy to know which response plans to implement and enable trend analysis during post-incident activities. Two common forms of classification strategies you should define in your plan include:
- Categories: Creating a standard set of descriptors (e.g., data breach, malicious code, social engineering, third party, etc.) helps group similar incidents, which can ultimately lead to better root cause analysis and comparative reporting.
- Severity: A scale to define the gravity of incidents should also be developed. A common scale is: Insignificant, Low, Medium, High, and Extreme. Assigning a severity level to incidents not only enables the organization to understand an incident's severity in relation to others, but it also allows handlers to prioritize response to more severe incidents before responding to lower impact events.
Creating classification strategies before an incident occurs can reduce difficult in-the-moment judgements, resulting in more efficient and accurate handling of an incident. Learn more in our blog: How to Classify Security Incidents for Easier Response.
3. Determine handling processes
Determining an incident handling process helps the organization establish a multi-phase, process-oriented approach for responding to an incident. In the Computer Security Incident Handling Guide, NIST defines six stages which should be included in your handling processes.
- Detection: How does your organization plan to detect potential incidents? Consider which system alerts, logs, publicly available information sources, and people you rely on to discover this information.
- Analysis: When a potential incident is detected, what steps do you take to confirm if it is an incident? This is usually performed through an assessment of the incident's scope, origins, and occurrence patterns. This information can then be paired with the classification strategies to best understand the incident.
- Containment: When an incident is declared, what can you do to isolate the incident and keep it from spreading? While this will largely depend on the nature of the incident and your environment, your goal should be to develop strategies that allow for effective containment, without affecting evidence preservation or operations.
- Eradication: After an incident has been contained, how will you find and eliminate any threats or vulnerabilities associated with the incident? Eradication strategies likewise depend on the incident itself, as well as the affected areas (e.g., systems, files, locations, etc.).
- Recovery: To recover from an incident, what steps will you take to restore operations to normal? While recovery is specific to the environment, it should include plans for bringing your systems and data back to baseline.
- Post-Incident: What can you learn from the incident and how can you use this information to improve future response processes? Often your post-incident activities should include generating a final report and holding a "lessons learned" meeting with affected parties.
The handling process is the heart of an effective incident management program. Developing the elements of your handling process will ensure incidents are addressed thoroughly and accurately when they occur. To learn more about determining your handling processes, check out our article over The Six Phases of an Effective Incident Response Plan.
4. Develop communication guidelines
Communication guidelines ensure the correct information is distributed to applicable parties during the right response stage. The communication guidelines should define who is authorized to communicate information on behalf of the organization and be clear about what, when, and with whom information should be shared. Here are three groups of people to keep in mind.
- Internal communication guidelines should define how to handle notifications of a potential incident, notifying affected personnel, and escalating the incident to senior management, when necessary.
- Third Party communication guidelines should define procedures for communicating with law enforcement, your primary federal regulator, information sharing agencies, vendors, etc.
- Customer communication guidelines should define approved communication channels (e.g., email, physical letter, press conference, webpage, etc.), the frequency of communications, and elements to include in a customer notification.
Having a predefined plan for the appropriate times and ways to communicate about an incident with these groups can reduce confusion during a hectic incident situation. Learn more in our blog: Incident Response Plan Communication Guidelines.
5. Outline evidence and forensics procedures
When an incident occurs, having procedures in place to detail how the organization plans to acquire, preserve, document, and store evidence is necessary. Your plans should outline how the incident response team will gather the evidence, expectations regarding evidence documentation (including chains of custody), and how long the evidence must be kept, for legal purposes.
You should also have a plan for engaging third-party forensics experts when external assistance is needed. Your plan should include up-to-date contact information for these third parties. You should also consider having prearranged service contracts and nondisclosure agreements to avoid negotiation delays, when feasible.
6. Create category-specific playbooks
When preparing for an incident, category-specific steps should be developed to guide responses. These playbooks are often referred to as "Action Plans." Grouping a series of steps to follow ensures incidents are managed in a standardized and authorized fashion. While it is not possible to develop a plan for every unique incident, there are standard steps the organization should follow for common events like phishing, ransomware, or third-party compromise.
7. Establish an incident tracking system
Every organization needs a streamlined way to document, track, and report on the status of their incidents, as they occur. Using an incident tracking system can improve communication, help ensure timely resolution, and provide accurate reporting. Check out our article on 5 Benefits of an Incident Tracking System for details.
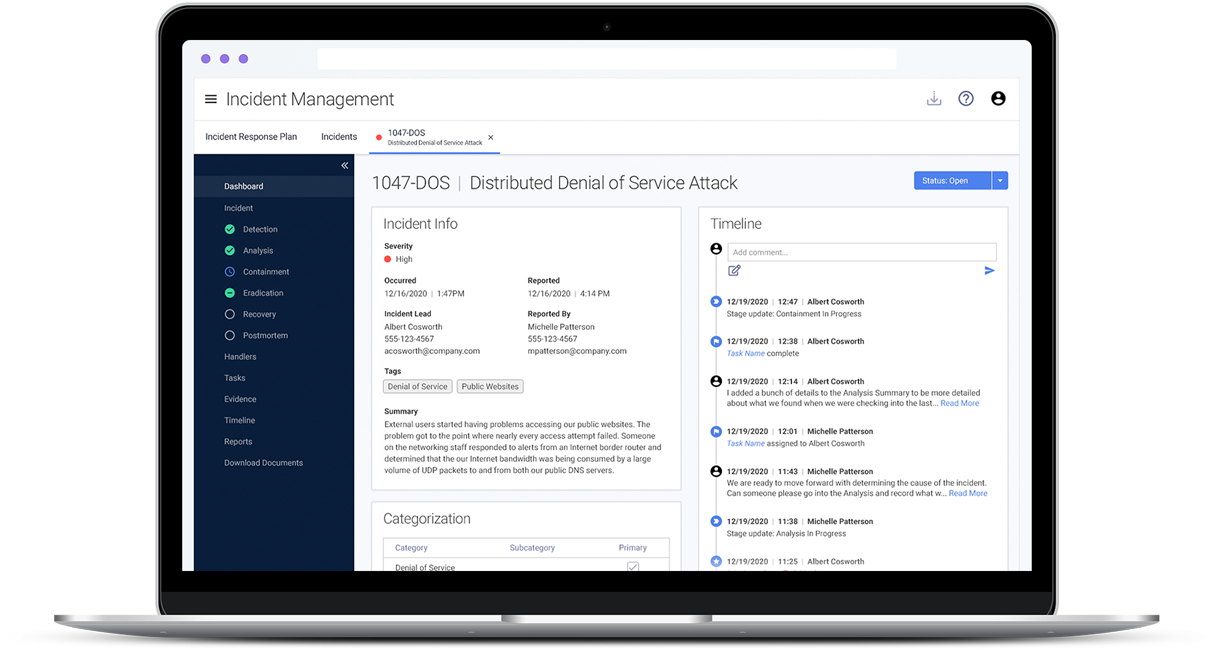
To formalize your security incident management program and tracking system, consider subscribing to an incident management application, such as Tandem Incident Management. In comparison to managing incidents and response plans using Word Documents and Excel Spreadsheets, Tandem offers a helpful interface for documenting incidents, following action plans, and downloading easy-to-read documentation. Learn more about Tandem Incident Management at Tandem.App/Incident-Management-Software.