"Quantum computing" started as a theory decades ago. Today it is becoming a reality with companies like IBM launching powerful quantum computers and the United States federal government issuing laws and guidelines on the topic.
So, let's look at why quantum computing is a cybersecurity risk, what requirements have been released so far, and what steps need to be taken to ensure compliance. Bookmark this blog and be sure to come back to see updates as the topic continues to evolve.
Why is Quantum Computing a Cybersecurity Risk?
Quantum computing is a cybersecurity risk because it has the potential to make today's encryption capabilities ineffective.
For example, let's say we encrypt our data today using strong encryption, like RSA 2048-bit encryption or AES 256-bit encryption. It is presumed that quantum computing will be able to break the encryption due to quantum's advanced computing power. This is a concern, in general, but it is especially concerning when it comes to data breaches. While breached data might be protected today due to its encrypted state, this may not always be the case.
It is only a matter of time before these supercomputers can perform mathematical calculations at such a level and speed that our present encryption is no longer sufficient to protect our systems and data.
Quantum Computing Timeline
The following is a timeline of key events related to quantum computing cybersecurity compliance. This is not intended to be a comprehensive list, but instead to provide an overview of the changing laws, regulations, and guidance on the topic.
Download the timeline infographic in PDF format.
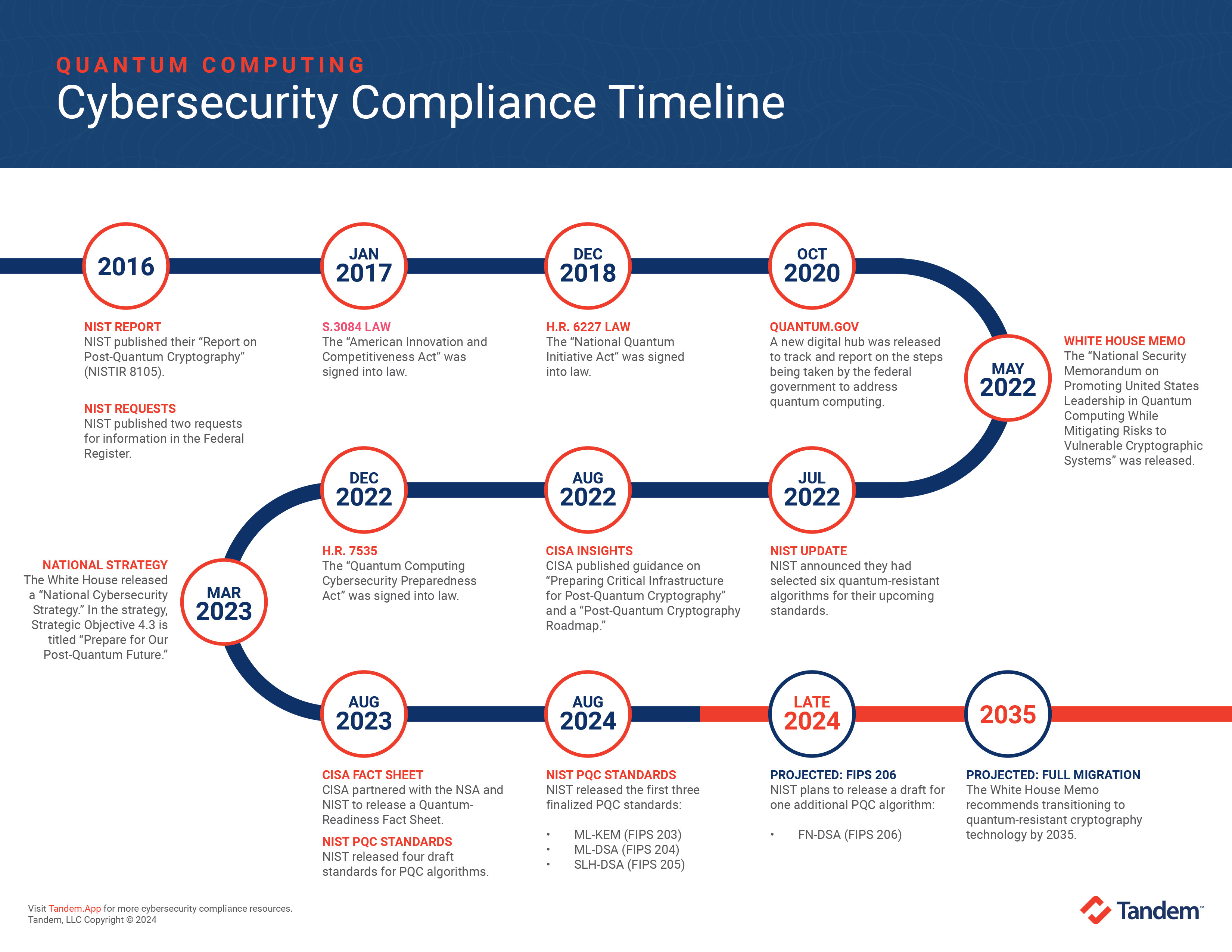
April 2016: NIST Report on Post-Quantum Cryptography
NIST has been researching, publishing, and presenting on post-quantum cryptography (PQC) with public materials as far back as 2011. NIST hosted a workshop on the topic in 2015. Then, in April 2016, things began to change. NIST published their Report on Post-Quantum Cryptography (NISTIR 8105). The findings were quite clear:
"Sufficiently large quantum computers will be built to break essentially all public key schemes currently in use. It has taken almost 20 years to deploy our modern public key cryptography infrastructure. It will take significant effort to ensure a smooth and secure migration from the current widely used cryptosystems to their quantum computing resistant counterparts."
Later that same year, NIST published two documents in the Federal Register:
- A Request for Comments on Post-Quantum Cryptography Requirements and Evaluation Criteria
- A Request for Nominations for Public-Key Post-Quantum Cryptographic Algorithms
The latter of these two documents was a request for help from the general public. The nominations NIST received from this request came to be significant in the development of PQC standards, as will be discussed later.
January 2017: American Innovation and Competitiveness Act
On January 6, 2017, the American Innovation and Competitiveness Act (S. 3084) was signed into law. This was the first bill signed into law that addressed the topic of PQC. Among other things, this law directed NIST to:
"Develop a process to research and identify, or if necessary, develop cryptography standards and guidelines for future cybersecurity needs, including quantum-resistant cryptography standards."
December 2018: National Quantum Initiative Act
On December 12, 2018, the National Quantum Initiative Act (H.R. 6227) was signed into law. This law was designed to "establish the goals and priorities for a 10-year plan to accelerate the development of quantum information science and technology applications."
This law expanded on the one from the previous year, giving NIST the legal directive to proceed with what they needed to develop PQC standards. It required NIST to:
"Carry out specified quantum science activities and convene a consortium to identify the future measurement, standards, cybersecurity, and other needs to support the development of a quantum information science and technology industry."
October 2020: Quantum.Gov and the Quantum Frontiers Report
On October 7, 2020, a press release was published that announced the launch of Quantum.Gov, a "new digital hub for the growing quantum community to connect with wide-ranging activities underway across the federal government." Along with the launch of the website, a Quantum Frontiers Report was published which was designed to ask questions and serve as a roadmap for quantum researchers.
May 2022: White House Memo on Quantum Computing
On May 4, 2022, the White House published a National Security Memorandum on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems.
"[The memorandum] identifies key steps needed to maintain the Nation's competitive advantage in quantum information science (QIS), while mitigating the risks of quantum computers to the Nation's cyber, economic, and national security. It directs specific actions for agencies to take as the United States begins the multi-year process of migrating vulnerable computer systems to quantum-resistant cryptography."
This memo explicitly mentions the impact quantum computing could have on the financial industry:
"When it becomes available, a [cryptanalytically relevant quantum computer] CRQC could jeopardize civilian and military communications, undermine supervisory and control systems for critical infrastructure, and defeat security protocols for most internet-based financial transactions."
The memo goes on to say that the United States must prioritize transitioning to quantum-resistant cryptography as much as is feasible by 2035, and that the first set of NIST's PQC standards are expected to be released by 2024.
July 2022: NIST Announces Quantum-Resistant Cryptographic Algorithms
On July 5, 2022, NIST published a press release. The article announced that NIST had chosen:
"The first group of encryption tools that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect privacy in the digital systems we rely on every day – such as online banking and email software."
These selected algorithms were announced following a six-year process, dating back to NIST's 2016 Federal Register publications. The algorithms are expected to be included as part of NIST's PQC standards.
August 2022: CISA Insights on Post-Quantum Cryptography
On August 24, 2022, the Cybersecurity and Infrastructure Security Agency (CISA) published guidance on Preparing Critical Infrastructure for Post-Quantum Cryptography. This resource provides an overview of the risks associated with PQC and introduces the Post-Quantum Cryptography Roadmap, developed by the Department of Homeland Security (DHS) and NIST.
September 2022: FFIEC & CISA Post-Quantum Cryptography Forum
On September 23, 2022, the Federal Financial Institutions Examination Council (FFIEC) and CISA collaborated to host a non-public virtual forum on "Preparing for Post-Quantum Cryptography." According to the FDIC's 2023 Report on Cybersecurity and Resilience, the forum addressed how PQC could "drive innovation across the economy, while highlighting the potential risk to the economic and national security of the United States."
December 2022: OCC Semiannual Risk Perspective for Fall 2022
On December 8, 2022, the Office of the Comptroller of the Currency (OCC) became the first federal banking agency to issue guidance on the topic of PQC to its supervised entities. The guidance was included in the Semiannual Risk Perspective for Fall 2022. The guidance reads:
"It is important for banks and their service providers to monitor how technological innovation may affect security controls. An example of emerging technology with security implications is quantum computing, which has the potential to render current encryption technology ineffective. While broad implementation of this technology will likely not be available in the near term, banks and service providers should be aware of the potential risk implications. The National Institute of Standards and Technology (NIST) has identified the first group of encryption tools that are designed to safeguard for risks posed by advances in quantum computing. Banks and service providers should consider how to effectively monitor these developments as they manage future infrastructure investments."
December 2022: RSA Podcast on A Quantum-Ready Board
On December 13, 2022, RSA Conference published a podcast interview on A Quantum-Ready Board: Governance and Cyber Risk Oversight. The podcast interviewed Maëva Ghonda and Dr. Lily Chen, the Head of Cryptographic Technology Group, Computer Security Division at NIST. (Dr. Chen was also one of the authors of the report published in 2016.)
Following a question that begins around the 18:00 minute mark, Dr. Chen said she anticipates the publication of NIST's PQC standards in 2023 for public comment and she expects finalization in 2024.
December 2022: Quantum Computing Cybersecurity Preparedness Act
On December 21, 2022, the Quantum Computing Cybersecurity Preparedness Act (H.R. 7535) was signed into law. The law requires each of the government executive agencies to create and maintain an inventory of all technology that may be vulnerable to decryption by PQC.
March 2023: National Cybersecurity Strategy
On March 2, 2023, the White House released the National Cybersecurity Strategy. Strategic Objective 4.3 is titled "Prepare for Our Post-Quantum Future." This objective identifies the nation's need to "prioritize and accelerate investments in widespread replacement of hardware, software, and services that can be easily compromised by quantum computers." It also references the May 2022 White House Memo for details on what this process will look like.
March 2023: FS-ISAC PQC Report
In March 2023, the Financial Services Information Sharing and Analysis Center (FS-ISAC) published a report titled Preparing for a Post Quantum World by Managing Cryptographic Risk. The document provides an overview of PQC, makes a business case for investing now, and offers a roadmap for PQC preparedness.
June 2023: FDIC Report on Cybersecurity and Resilience
On June 26, 2023, the Federal Deposit Insurance Corporation (FDIC) published their annual Report on Cybersecurity and Resilience. The report identified emerging risks associated with PQC, stating:
"While quantum computing promises greater computing speed and power, this technology could be utilized maliciously to compromise modern encryption methods. Financial technologies depend on modern encryption methods. Malicious actors cannot guess passwords and other keys using trial and error because current computing power does not allow them to succeed in a reasonable time. With the release of quantum computing into the public sector, current encryption methods may become inadequate."
July 2023: OCC Cybersecurity and Financial System Resilience Report
On July 19, 2023, the Office of the Comptroller of the Currency (OCC) published their annual Cybersecurity and Financial System Resilience report. The report identified emerging risks associated with PQC, stating:
"Quantum computing is an emerging technology with security implications that could make current encryption technology ineffective. While broad implementation of quantum computing is unlikely be available in the near term, banks and service providers should be aware of the risk implications and should consider how to effectively monitor developments in quantum computing as they manage future infrastructure investments."
August 2023: FRB Cybersecurity and Financial System Resilience Report
On August 1, 2023, the Board of Governors of the Federal Reserve System (FRB) published their annual Cybersecurity and Financial System Resilience report. The report identified emerging risks associated with PQC, stating:
"Quantum computing is another emerging risk area, as quantum computing capabilities could render current encryption standards used by financial institutions obsolete. The introduction of quantum cryptography will provide new solutions for protecting the integrity and confidentiality of data at rest and in transit but will also give threat actors new capabilities to avoid detection as well as permit data exfiltration. Hardware requirements and other factors may make the widespread implementation of quantum cryptography difficult currently, especially in legacy systems."
August 2023: FDIC 2023 Risk Review
On August 14, 2023, the Federal Deposit Insurance Corporation (FDIC) published their 2023 Risk Review. One of the risks highlighted by the document stated: "Quantum computing will pose new risks to critical infrastructure systems." The review continued:
"In general, traditional encryption relies on complex mathematical problems (encryption algorithms) that take an immense amount of time for classic computers to solve without knowing the encryption key. However, quantum computers use a different computing architecture that can solve certain types of problems much faster, including some encryption algorithms."
August 2023: CISA Quantum-Readiness Fact Sheet
On August 21, 2023, the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the National Institute of Standards and Technology (NIST) published a Quantum-Readiness: Migration to Post-Quantum Cryptography fact sheet.
The document provides guidance on topics like why businesses need to begin preparing now, establishing a quantum-readiness roadmap, preparing a cryptographic inventory, discussing post-quantum roadmaps with technology vendors, supply chain quantum-readiness, and technology vendor responsibilities.
August 2023: NIST Releases Draft Standards for Algorithms
On August 24, 2023, the National Institute of Standards and Technology (NIST) published draft standards for three of the four algorithms it selected in 2022 that are "designed to withstand attack by quantum computers." The four standards and their Federal Information Processing Standards (FIPS) are:
- CRYSTALS-Kyber (FIPS 203)
- CRYSTALS-Dilithium (FIPS 204)
- SPHINCS+ (FIPS 205)
- FALCON (FIPS coming in 2024)
October 2023: FINRA Report on Quantum Computing
On October 30, 2023, the Financial Industry Regulatory Authority (FINRA) published a report on Quantum Computing and the Implications for the Securities Industry. The purpose of the report is to "raise awareness among FINRA member firms and the broader securities industry by providing an overview of how developments in quantum computing may impact business models and processes."
December 2023: NIST Draft Guidance on PQC Migration
On December 19, 2023, the National Institute of Standards and Technology (NIST) published draft guidance titled NIST SP 1800-38: Migration to Post-Quantum Cryptography: Preparation for Considering the Implementation and Adoption of Quantum Safe Cryptography. The comment period closed on February 20, 2024.
May 2024: FDIC 2024 Risk Review
On May 22, 2024, the Federal Deposit Insurance Corporation (FDIC) published their 2024 Risk Review. The review reiterates and expands on comments from the 2023 version of the report. The review states:
"Quantum computing is expected to eventually render public, current encryption methods useless. The Cybersecurity and Infrastructure Security Agency, the National Security Agency, and the National Institute of Standards and Technology issued a joint factsheet to encourage the early planning for migration to postquantum cryptographic standards by developing a Quantum-Readiness Roadmap."
June 2024: NCUA Cybersecurity Report
On June 25, 2024, the National Credit Union Administration (NCUA) published their 2024 Cybersecurity and Credit Union System Resilience Report. The report highlights key risks to the credit union system, including quantum computing.
"The U.S. government remains concerned with the development and trajectory of quantum information technologies and products that could compromise existing encryption and other cybersecurity controls across critical infrastructure sectors."
July 2024: Congressional Report on PQC
In July 2024, the Office of Management and Budget issued a Report on Post-Quantum Cryptography to Congress. The report provided an overview of the current state of PQC, as well as perspectives on the future.
"Quantum computers show tremendous promise for the advancement of many fields, from pharmaceuticals to materials science. However, it is also likely that a sufficiently powerful quantum computer (a CRQC) will be able to break some forms of cryptography that are now commonly used throughout government and the private sector. A CRQC is not yet known to exist; however, steady advancements in the quantum computing field may yield a CRQC in the coming decade. Accordingly, while the U.S. Government continues to ensure the Nation's ability to maintain a competitive advantage in quantum computing, Federal agencies must also bolster the defense of their existing information systems by migrating to the use of quantum-resistant public-key cryptographic systems (PQC)."
August 2024: NIST Releases First Three Finalized PQC Standards
On August 13, 2024, the National Institute of Standards and Technology (NIST) published a final set of three post-quantum encryption standards. The press release states:
"The standards — containing the encryption algorithms' computer code, instructions for how to implement them, and their intended uses — are the result of an eight-year effort managed by NIST, which has a long history of developing encryption. The agency has rallied the world's cryptography experts to conceive, submit and then evaluate cryptographic algorithms that could resist the assault of quantum computers."
Along with NIST's announcement, the White House published a Fact Sheet on Post-Quantum Cryptography.
September 2024: Treasury Department Statement on Planning for Quantum Computing
In September 2024, the Department of the Treasury (as part of the G7 Cyber Expert Group (CEG)) released guidance on Planning for the Opportunities and Risks of Quantum Computing. According to the Federal Reserve's annual cybersecurity report to Congress:
"The G7 statement reflects growing concerns among international financial regulatory authorities that cyber threat actors will eventually be able to use quantum computers to defeat banks' current cryptographic techniques that secure communications and IT systems. The CEG encourages jurisdictions to monitor developments in quantum computing, to promote collaboration among relevant public and private stakeholders, and to begin planning for the potential risks posed by quantum computing on some current encryption methods."
October 2024: NIST Selected 14 Digital Signature Candidates
On October 25, 2024, the National Institute of Standards and Technology (NIST) announced 14 digital signature candidates as part of the PQC Standardization Process. The candidates are detailed in NIST IR 8528, Status Report on the First Round of the Additional Digital Signature Schemes for the NIST Post-Quantum Cryptography Standardization Process.
November 2024: Protecting Payments in the Quantum Era
On November 4, 2024, Nacha's Payments Innovation Alliance published a report on Protecting Payments in the Quantum Era: What You Need to Know. According to the press release:
"This free publication outlines the basics of quantum computing, explaining key concepts and how it differs from classical computing. It explores the potential applications of quantum computing in the financial sector, particularly in payments, highlighting opportunities for innovation and efficiency. The report also addresses the significant threats quantum computing poses to current cryptographic standards and discusses recent developments in quantum technologies, the urgent need for quantum-safe cryptographic solutions and the next proactive steps to prepare payments industry leaders for the quantum era."
November 2024: NIST IR 8547 Draft Published
On November 12, 2024, the National Institute of Standards and Technology (NIST) published the initial public draft (IPD) for NIST IR 8547 Transition to Post-Quantum Cryptography Standards.
"This report describes NIST's expected approach to transitioning from quantum-vulnerable cryptographic algorithms to post-quantum digital signature algorithms and key-establishment schemes. It identifies existing quantum-vulnerable cryptographic standards and the current quantum-resistant standards that will be used in the migration."
Comments are welcome on the draft through January 10, 2025.
December 2024: OCC Semiannual Risk Perspective for Fall 2024
On December 16, 2024, the Office of the Comptroller of the Currency (OCC) published updated guidance on the topic of PQC for its supervised entities. The guidance was included in the Semiannual Risk Perspective for Fall 2024. The guidance reads:
"The OCC continues to monitor the progress toward quantum computing capabilities and the associated risks to general encryption techniques. On August 13, 2024, the National Institute of Standards and Technology (NIST) finalized its principal set of encryption standards designed to withstand cyberattacks from a quantum computer. The new standards are designed for general encryption and digital signatures, which are critical to protect information and authentication. The process for transitioning to these new post-quantum computing (PQC) standards will likely take years to fully test and implement. Banks are encouraged to conduct inventories of where encryption is used within their operations and work with third parties to assess their PQC transition plans to ensure long-term security and interoperability. Institutions that develop their own software are also encouraged to begin the migration process."
January 2025: White House Executive Order
On January 15, 2025, the White House published a new Executive Order on Strengthening and Promoting Innovation in the Nation's Cybersecurity. The order promoted the adoption of PQC technologies.
"Although the timeline for achieving a large-scale quantum computer is still uncertain, a quantum computer of sufficient size and sophistication will be able to break the public-key cryptosystems currently in use, allowing an attacker to decrypt encrypted communications and impersonate users and servers. In August of 2024, NIST standardized new post-quantum cryptographic (PQC) algorithms which are designed to resist attack by quantum computers. This Executive Order accelerates the transition of Federal cryptographic systems to use PQC through the following actions:
-
- Requires agencies to enable quantum-resistant key establishment within their existing networks, protecting government communications from being recorded now for decryption once a CRQC exists.
- Identifies PQC-capable products and requires that agencies purchase them once they become widely available, protecting the US Government and helping grow the global market of post quantum technologies."
March 2025: NIST Selects Fifth PQC Algorithm
On March 11, 2025, NIST announced they had selected HQC as a Fifth Algorithm for Post-Quantum Encryption. According to the announcement:
"Last year, NIST published an encryption standard based on a quantum-resistant algorithm called ML-KEM. The new algorithm, called HQC, will serve as a backup defense in case quantum computers are someday able to crack ML-KEM. Both these algorithms are designed to protect stored information as well as data that travels across public networks."
HQC joins the existing four PQC algorithms: FIPS 203 (ML-KEM), FIPS 204 (ML-DSA), FIPS 205 (ML-DSA), and FIPS 206 (FN-DSA). While the first three were finalized in August 2024, the draft for FIPS 206 has not yet been published.
July 2025: OCC Cybersecurity and Financial System Resilience Report
In July 2025, the OCC published their annual Cybersecurity and Financial System Resilience Report to Congress. The report highlights post-quantum cryptography as a current and emerging risk.
"Quantum computing is an emerging technology with security implications that could make current encryption technology ineffective. While broad implementation of quantum computing is unlikely to be available in the near term, banks and service providers should be aware of the risk implications and should consider how to effectively monitor developments in quantum computing as they manage future infrastructure investments."
July 2025: FRB Cybersecurity and Financial System Resilience Report
In July 2025, the FRB published their annual Cybersecurity and Financial System Resilience Report to Congress. The report mentions a recent training for IT examiners that addressed "quantum resilience." It also identified quantum computing as a "significant emerging risk area."
"Quantum computing is another significant emerging risk area on the horizon, as quantum computing capabilities could render current encryption standards used by financial institutions obso- lete. The introduction of post-quantum cryptography will provide new solutions for protecting the integrity and confidentiality of data at rest and in transit. Several federal agencies have highlighted steps that institutions can take now to prepare for the cryptographic risks associated with quantum computing. For example, in 2023, the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency, and National Institute of Standards and Technology (NIST) published "Quantum-Readiness: Migration to Post-Quantum Cryptography," which informs institutions about quantum capabilities and promotes a proactive approach for institutions to take now by instituting a "Quantum-Readiness Roadmap" to prepare for post-quantum cryptography migration. NIST finalized its initial set of quantum-resistant encryption algorithms in August 2024."
What's Next?
Three words: Start preparing now. Here are three recommendations to help get you started.
- Educate. We need to educate ourselves. We also need to educate the decision-makers at our organizations, including senior management and Boards of Directors. Keep an eye on this blog for future regulatory updates. For some extra resources on how to stay on top of this topic, check out the "Additional Resources" section below.
- Inventory. We need to identify our most critical systems and data and determine what risk of PQC compromise they face. Prioritize the inventory based on things like the criticality of the system and its data, any interdependencies, or what functions the system fulfills.
- Discuss. We need to start a conversation about what it may look like to upgrade or replace those systems with modern, quantum-resistant technology. If these infrastructure investments are not on your 10-year plan, it would be good to start including those in future strategic conversations and conversations with your vendors.
Quantum computing technology is evolving. We need to do what we can now to make sure we keep up.
As quantum computing regulations and guidance continue to evolve for financial institutions, Tandem will help create resources to support you and your business. Learn more about how Tandem can help with your cybersecurity governance, risk management, and compliance (GRC) practices today at Tandem.App.
Additional Resources
For additional information about PQC, check out the following resources:
- DHS Post-Quantum Cryptography Roadmap
- CISA Post-Quantum Cryptography Initiative
- NIST Computer Security Resource Center: Post-Quantum Cryptography
- National Quantum Initiative
- Quantum Computing: A Cybersecurity Compliance Timeline (PDF)
- FS-ISAC Preparing for a Post-Quantum World by Managing Cryptographic Risk Report