When you search the web for the "definition of risk," you will likely be greeted by a series of images which look something like this.

Nothing quite conveys the meaning of "risk" like a yellow warning sign with a biological, radioactive, or electrical hazard emblem. I especially like the one that looks like it's covered in some kind of debris. The implication being if you take on risk, you've already elected to walk through the nuclear fallout. (Very nice.)
While a picture may be worth a thousand words, the dictionary apparently only needs five.
- Merriam-Webster defines risk as the "possibility of loss or injury."
- Oxford defines risk as a "situation involving exposure to danger."
- Wikipedia defines risk as the "possibility of something bad happening."
Our definitions of the word "risk" stem from the 17th century Italian word "risco" meaning "danger," although it's use in publications did not become mainstream until the 1960's according to Google Books Ngram Viewer.
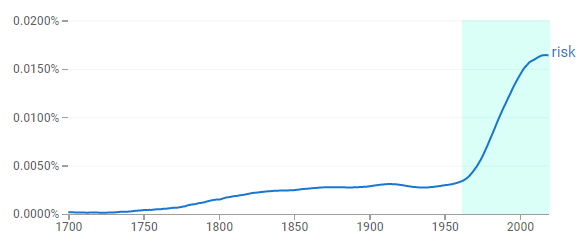
With images and definitions like these, "risk" seems like a very bad thing, and something which should be avoided at all costs… right? Well, not necessarily.
A new definition of the word "risk" has begun to emerge as the preferred definition du jour, especially as it relates to cybersecurity risk. Originally published in 2009, the ISO 31000 standards likewise use five words to define risk as the "effect of uncertainty on objectives." This definition has been increasingly adopted in government agency publications, including the Office of Management and Budget (OMB) Circulars A-11 and A-123 and in the National Institute of Standards and Technology (NIST) Internal Report 8286.
When the concept of danger is removed from the definition of risk, it opens the door to a world full of wild potential. The publications refer to this positive view of risk as "opportunities."
The FFIEC emphasizes this concept of "opportunity" repeatedly in their new Architecture, Infrastructure, and Operations (AIO) booklet. To make the most of these opportunities, the booklet recommends:
- A clear governance structure. Specifically, it encourages designating a role titled "Chief Data Officer" (CDO) who would help the organization "perform more efficiently, improve productivity and revenue, and create business opportunities and innovation." (Page 9)
- Strong leadership. The booklet (and Examination Objective 17) states, "management should develop processes to oversee operations functions, evaluate the effectiveness of controls, and identify opportunities for improvement." (Page 83, 129)
- Planning for potential. Altogether, we see opportunistic terms like "future," "interoperability," "flexibility," "scalability," "portability," and "capacity" scattered throughout the booklet a total of 140 times.
What all of this tells us is there is a heightened expectation around positive cybersecurity risk as part of the overall business strategy. It starts with identifying opportunities and planning for growth, which may not be as foreign of a concept as you might initially think.
For example, think about the last time you wanted to implement:
- A new software application. The positive risk (opportunity) to do your job more effectively and efficiently might have outweighed the negative risk (threat) of things which could go wrong with the app.
- A new third-party relationship. The positive risk (opportunity) to obtain a service at a more cost friendly price-point might have outweighed the negative risk (threat) of switching third parties.
- A new security control. The positive risk (opportunity) to better secure your systems and data might have outweighed the negative risk (threat) of team members experiencing roadblocks in their daily jobs.
Opportunities make it possible for us to improve our businesses and ourselves. This isn't to say threats don't exist. On the contrary, we know they are very real and must be assessed and managed accordingly. That said, as an industry which has primarily operated from a threat-centric viewpoint, we can forget to look on the bright side, innovate, and grow.
What are you doing to assess and manage your cybersecurity opportunities?


