In October 2020, the National Institute of Standards and Technology (NIST) published NISTIR 8286 over Integrating Cybersecurity and Enterprise Risk Management (ERM). The document provides an overview of ERM and how cybersecurity should be integrated with ERM to ensure the organization is better able to recognize, assess, and control risk across the organization.
In this article, we will summarize some of the key concepts presented in the NIST document and discuss questions like:
- What is ERM?
- What are some challenges with ERM?
- What does ERM look like?
- Why is integrating cybersecurity and ERM important?
- Will Tandem develop a tool for ERM?
What is ERM?
According to the Office of Management and Budget (OMB) Circular No. A-11, as quoted by NIST, ERM is "an effective agency-wide approach to addressing the full spectrum of the organization's significant risks by understanding the combined impact of risks as an interrelated portfolio rather than addressing risks only within silos."
Several times in this definition, we see broadly scoped words like "agency-wide," "full-spectrum," "combined impact," and "interrelated portfolio." In other words, ERM is the process of rolling all risk data together to provide senior management with context so they can make the necessary decisions to ensure the organization survives and thrives.
What are some challenges with ERM?
There are several challenges with implementing an effective ERM program. Some of the challenges you may experience include:
- Lack of standardization. Each "silo" within an organization calculates risk differently. For example, while an information security risk assessment may evaluate a threat's likelihood and impact to the confidentiality, integrity, and availability of information, an interest rate risk assessment may involve complex calculations and thresholds. Risk is assessed in both scenarios, but it requires specific knowledge and formats to perform and extrapolate meaning from these types of assessments.
- Lack of resources and expertise. In smaller organizations, there may not be the resources or staff expertise to designate a singular role as responsible for ERM. In situations like these, it can be beneficial to create a risk management committee with representation from various divisions to share, discuss, and report on risks facing the enterprise.
- Lack of guidance. While there are several frameworks and resources, there is limited regulatory guidance on the topic, especially for financial institutions. While the FFIEC has begun to address ERM in its Management and Architecture, Infrastructure, and Operations booklets, the language of the guidance is more descriptive than prescriptive. The guidance describes what institutions should do while providing limited support in describing how institutions can get there.
Despite challenges like these, there are ways in which ERM can be accomplished and cybersecurity plays a key role in this picture. This is where the NIST document shines.
What does ERM look like?
Table 1 in the NIST document (Page 7) provides a detailed mapping of the similarities among several ERM and risk management frameworks. It maps each to a standardized process that involves six core phases.
- Identify the context. What makes up the environment in which you are assessing the risks?
- Identify the risks. Which events could have an impact on your ability to achieve a certain goal?
- Analyze the risks. What are the likelihood and potential impact of the events?
- Prioritize the risks. Based on the likelihood and potential impact, which risks are more significant than others?
- Plan and execute response strategies. What will you do to manage the risks?
- Monitor, evaluate, and adjust. How will you manage the risks over time?
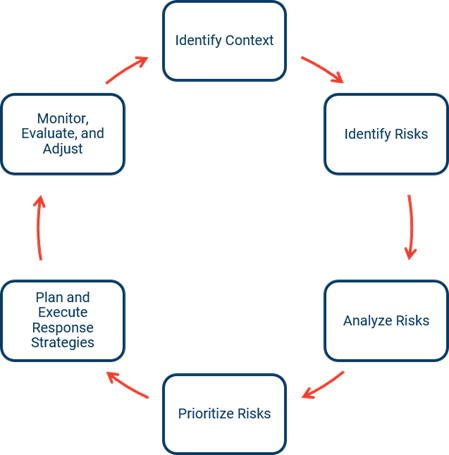
To effectively perform these functions in an ERM context, the NIST document recommends a two-step process:
- Use a risk register for each "silo" in the organization. According to OMB Circular No. A-11, a risk register is "a repository of risk information including the data understood about risks over time. […] Typically, a risk register contains a description of the risk, the impact of the risk should occur, the probability of its occurrence, mitigation strategies, risk owners, and a ranking to identify higher priority risks." Tandem Risk Assessment is an example of a risk register, designed and created specifically for information security risk management.
- Prioritize significant risks from all risk registers into a risk profile. According to OMB Circular No. A-123, a risk profile is "a prioritized inventory of the most significant risks identified and assessed through the risk assessment process versus a complete inventory of risks." Someone with a birds-eye view of the organization, such as a Chief Risk Officer or risk management committee, should look at the most significant risks across the organization, consolidate the data into an enterprise risk profile, and use this information to inform senior management of the truly significant risks facing the enterprise.
Not sure where to get started? Download this ERM Template Excel Spreadsheet to see a risk register based on the examples presented by NIST.
Why is integrating cybersecurity and ERM important?
According to the NIST document:
"When [an] organization or enterprise receive[s] system cybersecurity risk data, it is often a perpetually red heatmap or at such a volume as to be impractical. Therefore, it is not surprising that higher levels of an organization or enterprise tend to struggle with understanding cybersecurity risk."
In other words, cybersecurity data can be overwhelming and does not often communicate meaningful data when it remains in its own silo. Cybersecurity data is more effectively communicated in the context of the business value it provides, which is where ERM comes in.
For example, consider the case of a lost or stolen laptop. This is not an unimaginable risk for a cybersecurity specialist to consider, especially in a time when remote environments are becoming more common. Now, imagine the laptop contained significant intellectual property. Theft of such an asset extends far beyond the cost of simply replacing a laptop. Some downstream effects could include a loss of competitive advantage, negative reputation, falling share prices, loss of future revenue, and beyond.
While a cybersecurity specialist may be able to assess the risk of a lost or stolen laptop, ERM affords someone at a higher level the opportunity to see the big picture and assess additional operational, compliance, financial, and strategic impacts of such an event's occurrence.
Will Tandem develop a tool for ERM?
At Tandem, it is our goal to improve security while easing the burden of regulatory compliance, and we are honored to have so many financial institutions contacting us for assistance in managing this topic.
Our current solutions focus largely on topics related to information security, vendor management, business continuity, incident response, cybersecurity, and IT. While these are influential components of ERM, there are other "silos" in which we do not currently provide the same level of consulting and expertise through our existing offerings. As such, ERM is currently outside the scope of our products.
We believe Tandem Risk Assessment plays a significant role in helping you understand the information security and cybersecurity risks facing your organization's assets and data. In addition, Tandem Cybersecurity (based on the FFIEC Cybersecurity Assessment Tool) can help you assess your organization's cybersecurity risk and control maturity. Tandem is designed to make it easy to identify, analyze, and prioritize risks and access the information needed to report on significant cybersecurity risks across the organization.
That said, we understand there is a need for an easy-to-use ERM solution designed to support community financial institutions, and it is something Tandem leadership continues to evaluate. If you would be interested in an ERM solution from Tandem, please email [email protected].
In Summary
ERM is foundational to an organization's ability to understand risk within the context of the business. Significant cybersecurity risks should be incorporated into the organization's ERM function to ensure the risks are given the appropriate consideration by senior management.
If you are looking for a tool to help you identify, measure, control, and monitor your information security and cybersecurity risks, check out Tandem Risk Assessment and Tandem Cybersecurity. Tandem can help ensure you have what it takes to manage your cybersecurity risks while making it easy to share results with those responsible for ERM at your organization.


